Blog
Bypassing Object Detection: The Art of Login Text Manipulation in Phishing Attacks
By BUFFERZONE Team
Target: IT Professionals (Elementary)
Tags: Phishing, Safe Workspace®, Safe Browsing, NoCloud® Anti-Phishing, Object Detection, Protection by containment™
Phishing attacks are a persistent threat in the ever-evolving landscape of cybersecurity. Attackers use various techniques to deceive unsuspecting users into revealing sensitive information, such as login credentials. One technique that is gaining popularity is bypassing object detection systems by manipulating the login text information. This manipulation of login text information is a significant step in recognizing a phishing attack. Attackers use different ways to camouflage the login page, making it difficult to detect. However, object detection is a promising solution to overcome this issue. In this blog, we will discuss the critical need for robust object detection capabilities in detecting phishing attacks. We will explore how attackers manipulate login text to evade detection and increase success rates.
The Importance of Object Detection in Phishing Detection
Object detection plays a pivotal role in modern cybersecurity defenses, especially in the context of phishing detection. With the proliferation of sophisticated phishing attacks, automated systems equipped with object detection capabilities have become indispensable tools for identifying and thwarting such threats.
Object detection systems use advanced algorithms based on Deep Learning models to analyze images and detect specific objects or patterns. In the context of phishing detection, these systems are adept at recognizing elements such as login screens, password fields, brand logos, and other sensitive information commonly targeted by attackers.
Bypassing Object Detection Through Text Manipulation
Phishing attackers are adept at exploiting vulnerabilities in security systems, and one increasingly prevalent tactic involves manipulating login text information to bypass object detection mechanisms. Here’s how attackers execute this technique:
Text Obfuscation: Attackers may obfuscate login text by applying transformations such as rotating, skewing, or distorting characters. These alterations make it challenging for object detection algorithms to accurately extract text from phishing images.
Background Noise Addition: Another tactic involves adding background noise or clutter around login text elements. By blending text with surrounding visual elements, attackers disrupt the clear delineation between text and background, making it harder for object detection systems to isolate and recognize login information.
Overlay Techniques: Attackers may overlay transparent images or patterns on top of login text, obscuring it from object detection algorithms. This technique exploits the limitations of image analysis algorithms, which may struggle to differentiate between legitimate text and overlay artifacts.
Font Manipulation: Altering the font style, size, or color of login text can also confound object detection systems. By employing unconventional fonts or color schemes, attackers introduce additional complexity, making it more difficult for automated systems to identify and extract login information accurately.
Homoglyph Substitution: This is a technique where attackers replace characters with visually similar alternatives to obfuscate the original text. This can make it more challenging for detection systems to recognize sensitive information, such as passwords, especially in the context of phishing attacks.
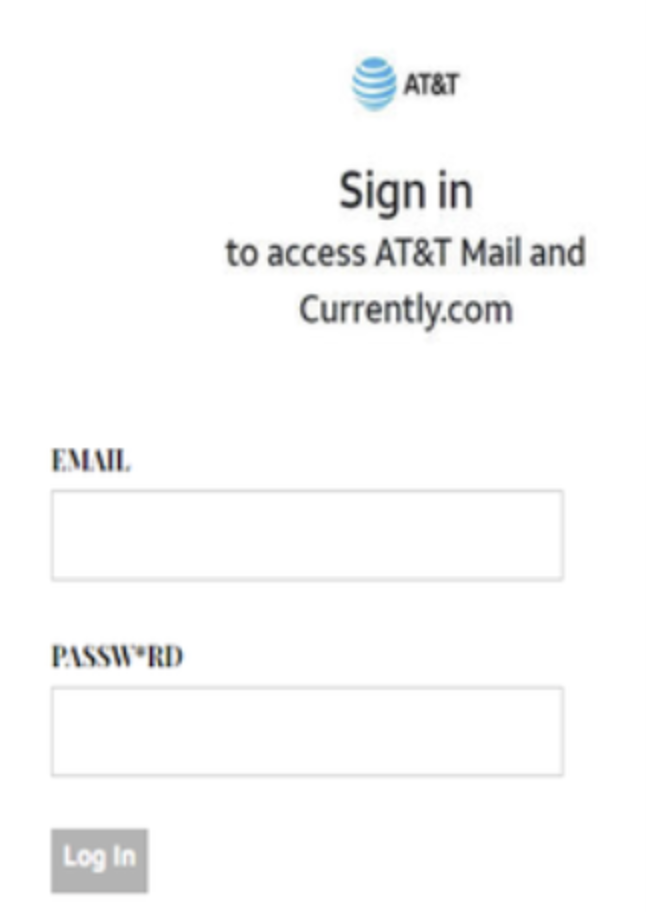
For example, a fake AT&T login page manipulates the PASSWORD to PASS*RD between others.
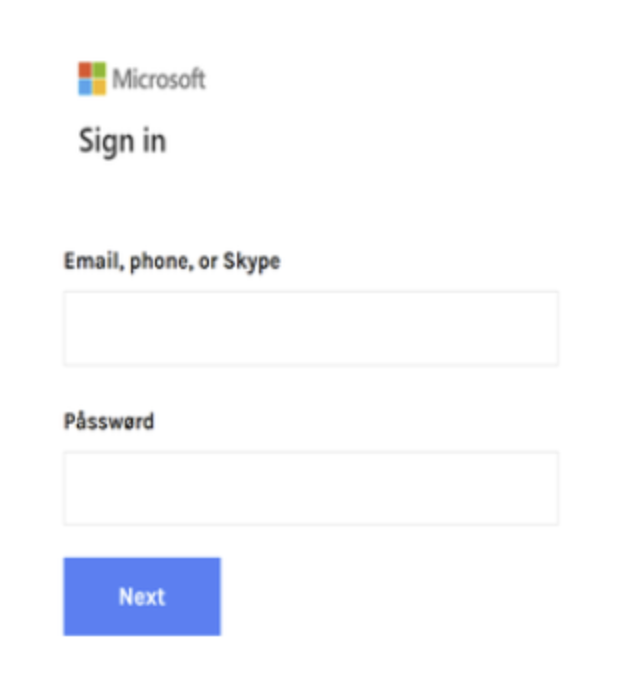
An alternative can be seen in this fake Microsoft Login page where homoglyphs for “a” and “o” are used.
Implications and Countermeasures
The manipulation of login text to bypass object detection poses significant challenges for cybersecurity defenders. As attackers continuously refine their tactics, organizations must enhance their detection capabilities and adopt proactive measures to combat phishing threats effectively.
To mitigate the risks associated with text manipulation in phishing attacks, organizations can implement the following strategies:
Advanced Object Detection Techniques: Improve object detection algorithms to adapt to evolving attack tactics. This may involve using deep learning models trained on diverse datasets to enhance the accuracy and robustness of detection systems.
Anomaly Detection: Augment object detection with anomaly detection techniques to identify suspicious patterns or inconsistencies in phishing images. By flagging deviations from expected norms, anomaly detection mechanisms can help uncover sophisticated attack attempts.
User Education and Awareness: Educate users about vigilance and skepticism when interacting with online content. Empower users to recognize phishing indicators such as unusual login prompts or suspicious website URLs, reducing the likelihood of falling victim to phishing attacks.
Multi-Layered Defense Mechanisms: Implement a multi-layered security approach that combines object detection with other security measures such as email filtering, web content filtering, and behavioral analysis. By deploying complementary defense mechanisms, organizations can effectively create multiple barriers to thwart phishing attempts.
In conclusion, manipulating login text to bypass object detection is a significant challenge in the ongoing battle against phishing attacks. By understanding the tactics employed by attackers and implementing robust detection and mitigation strategies, organizations can bolster their defenses and minimize the risks posed by these insidious threats.
Are you interested in learning more?

















