Blog
Stop Worrying and Start Isolating – Darkgate Malspam Is Back
By BUFFERZONE Team
Target: IT Professionals (Elementary)
Tags: Phishing, Safe Workspace®, Safe Browsing, NoCloud® Anti-Phishing, Protection by containment™
DarkGate malware attacks are spread through spam emails containing malicious attachments or links.
This threat is called Malsam. It is a way to deliver malware or other harmful
software to a victim’s computer or network. DarkGate Malspam campaigns often use emails with attachments like Microsoft Office documents, PDF files,
or ZIP archives.
These attachments are designed to exploit vulnerabilities or deceive users into opening them. Once opened, the malware can install backdoors, keyloggers, ransomware,
or other
malicious software on the victim’s system.
Discovered by a security researcher (@Tac_Mangusta, Link), the new attack infection process for this campaign starts with an email file that has an HTML attachment
(Figure. 1).
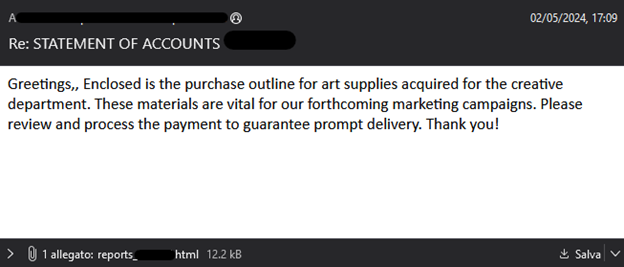
Figure. 1 Email lure with HTML file attachment (source Link)
The HTML file looks like a blank Microsoft Document with instructions on fixing offline viewing. This is a trick to get victims to paste malicious PowerShell code into a
Windows Terminal as can be seen in Figure. 2.
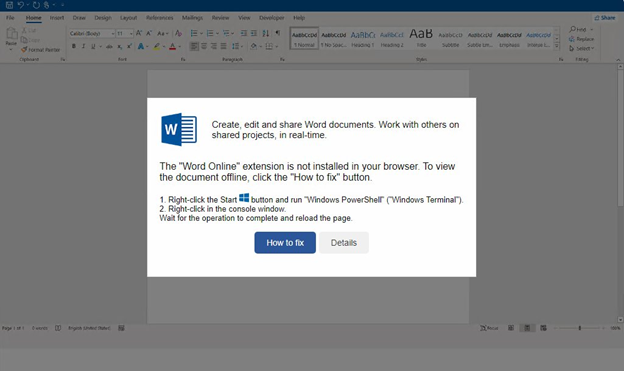
Figure. 2 HTML lure with clicked How to fix instruction that looks like Microsoft Word file (source Link).
Once the code is executed, an HTA file will be downloaded and will continue to execute, eventually downloading a follow-up ZIP file. Once extracted, the ZIP file will launch
an open-source automation engine called AutoIt to execute a malicious AutoIt script named script.a3x that will eventually load the DarkGate trojan.
Staying Safe in the Digital World
To combat this threat, individuals and organizations must adopt preventive security measures. This includes educating employees about the signs of phishing emails, implementing
advanced security solutions, and regularly updating systems to patch vulnerabilities. However, 92% of the attacks start with phishing attacks targeting the human factor.
However, this attack used a simple lure text and malicious phishing link.
This is why we created BUFFERZONE® Safe Workspace®, a suite of zero-trust solutions that it’s strategic concept is Protection by containment™, it consists of Safe Mail, NoCloud® Artificial Intelligence (AI) Anti-Phishing, SafeBridge®
Content Disarm and Reconstruction (CDR), and Safe Browser, a secure browsing solution.
Safe Mail is a Microsoft Outlook plugin that uses BUFFERZONE® SafeBridge® to CDR emails and open links and attachments securely inside a BUFFERZONE® secure virtual container. BUFFERZONE® container isolates the browsing and file activity while keeping your computer safe from evasive attacks. In this sophisticated Malspam attack example, the fake HTML file
that looks like a Word file will be opened inside our container and will be unable to execute its malicious second step, will be isolated from the organization environment.
As a result, the next step of the attack is stopped, and the human factor security breach is minimized.
Conclusion
Phishing and evasive malware are always finding new innovative ways to bypass detection. By isolating threats and adding prevention capabilities to your existing detection solution
with an intelligent phishing detection solution, the organization achieves the highest level of security and keeps IT simple.

















