Blog
APT malware spread illustrates need to add prevention to protect native endpoint
By BUFFERZONE Team, 24/01/2023
Advanced Persistent Threat (APT) attacks are becoming a growing threat to governments and other large institutions.
APT malware is extremely vicious as it is hard to detect and can remain idle on the organization network for a long time without being traced. APT attacks are usually conducted to steal large amounts of data from institutions with high-value information, such as government, military, and the financial industry and are a set of stealthy and continuous hacking processes.
What makes APT such a dangerous attack is the fact that sometimes it is not detected for months or even years. APT gangs are using a wide variety of tools and techniques to penetrate networks and conceal their presence for long periods of time. Attackers may use malware, spyware, root or boot kits, network propagation mechanisms, and sophisticated social engineering strategies like spear-phishing or whaling.
The elusive nature of APT attacks requires adopting new security tactics, which do not rely on discovery and detection but rather on protection.
The latest evidence of the threat APT poses was illustrated earlier this month following the discovery of a series of cyberattacks against government and military targets in Southeast Asia, by cyber security company Group-IB. This notorious group has already breached the cyber defenses of six organizations in Cambodia, Indonesia, Malaysia, Philippines, and Vietnam.
One of the most sophisticated APT-based gangs launched an attack using a PowerPoint file that exploited a code execution technique, which was designed to be triggered when the user starts the presentation mode and moves the mouse.
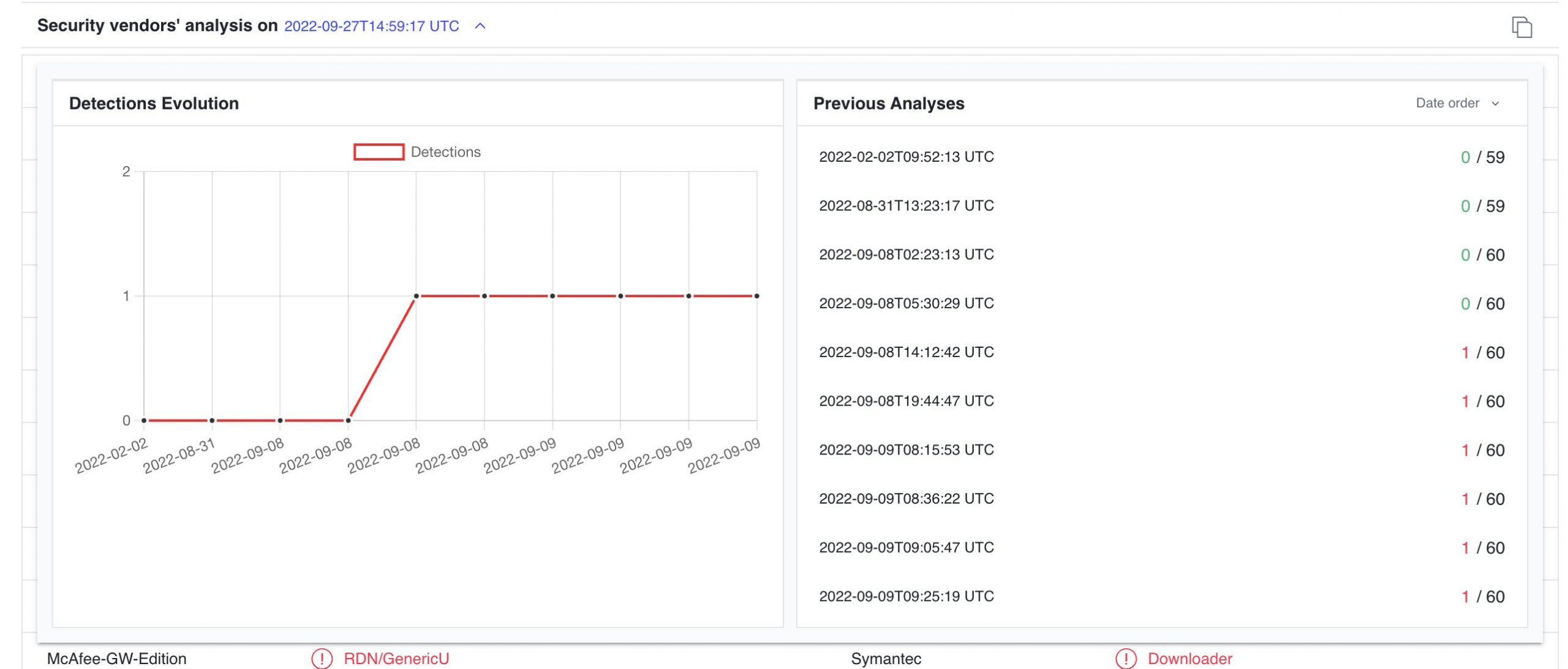
APT threat that wasn’t detected for months. Source InQuest.
By using solutions such as BUFFERZONE, security experts can dramatically lower the APT threat.
BUFFERZONE provides a safe workspace by keeping access to external, untrusted content such as unknown websites, external email messages, and removable media in a virtual container, along with anything saved or downloaded.
Contained browsing sessions and applications cannot reach the native endpoint or organizational resources such as an intranet; those are accessed only by uncontained browsing sessions and applications, which can’t access untrusted sites. As needed, contained content can be disarmed by BUFFERZONE’s SafeBridge of active, risky components and securely moved out of the container. This can happen automatically by policy, or manually by users.
The advantage of this approach is clear: When an APT malware strikes, no matter how new it is and what evasion techniques it implements – it cannot cause any damage to the native endpoint or organizational resources.

















