Blog
Fake Updates: Taking Advantage of Responsible Users
By BUFFERZONE Team, 5/11/2019
These days, even relatively unsophisticated users are aware of the significant dangers posed by computer malware and are aware of the need to protect their assets against it. And one of the basic defensive measures that we’re frequently correctly told to take is to always update our software, to make sure it includes any possible security patches and fixes. Otherwise, we know, hackers may exploit known software vulnerabilities.
Unfortunately, the hackers know this as well. And they’re mercilessly taking advantage of it. Especially over the last year or two, as reported by several malware researchers (see Sources below), browser users have seen several different types of fake messages prompting them to update their browsers. The following are a couple of examples.
Firefox:
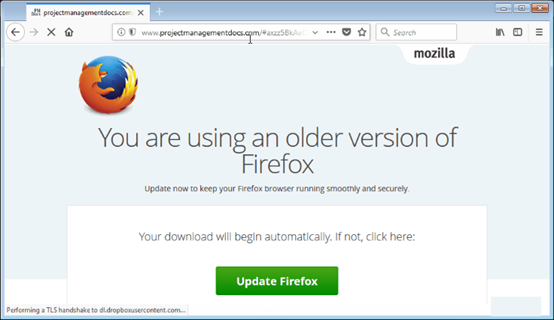
Chrome:
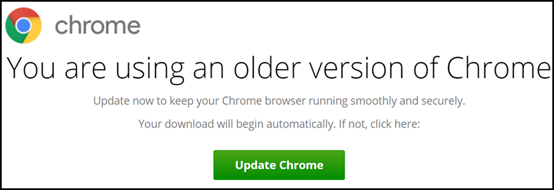
Browser users conscientiously click to update their browsers. As you may have guessed by this point, when the user clicks to update, what is actually downloaded is malware. The malware’s payload varies. Sometimes it’s a Remote Access Tool enabling the hackers to take full control of the computer, other times it’s ransomware or a trojan that steals bank credentials.
Here we’ll explain in a bit more depth how these exploits work, and defense against them.
How Does it Work?
The exploit begins with a legitimate website whose host CMS (Content Management System, such as WordPress or Joomla) has been hacked. The hack causes the site to display the update message to site visitors. Relevant update messages are displayed for Chrome or Firefox.
Upon clicking to update, the initial download typically includes Javascript code. The Javascript communicates with the attackers’ control server and downloads a payload with an additional Javascript file – update.js , which with the help of the Windows wscript.exe executes the payload.
Multi-layer code obfuscation and encoding is applied throughout, to make it difficult for endpoint security products and for analysts to identify the malware. Malware persistence is often ensured through registry settings or a Startup shortcut.
Some possible payloads include the NetSupport Remote Access Tool (RAT), ransomware, Dridex banking malware (possibly the most common), AZORult, and Chthonic.
Defending Against Fake Updates
The easiest way to defend against fake updates is of course simply to avoid falling for the fake update ruse. Make sure to only download updates that are clearly coming from the software vendor’s website.
However, if you’re responsible for the endpoint security in an organization, you probably already know that relying on your users’ strictly adhering to this guideline is not a good idea. Conventional endpoint security products do often identify the malware, once downloaded, and protect against it. However, both signature-based and analysis-based security products have limited success. Given the cybercriminals’ consistent attempts to evade and circumvent the security products by continuously evolving this and other types of malware, some inevitably get past them.
Fake updates are just an example of many such changing and developing malware types. Gradually, attitudes among the security establishment are moving from the outdated model of relying on detection to recognition of the need for proactive containment and isolation.
BUFFERZONE provides exactly such a solution. If the fake updates, or other malware, is downloaded to an endpoint protected by BUFFERZONE, it is automatically isolated with all such downloads inside a virtual container, where it can do no lasting harm. It cannot affect the native endpoint, and cannot read any trusted data. To safely access banking sites, organizations need only to define banking sites in their Trusted list, and those network connections and data are kept completely separate from any possible downloaded malware. BUFFERZONE users can confidently open any received shipping documents, invoices, or other documents, secure in the knowledge that the activity is safely contained.
Don’t wait for the next new attack. Protect your organization now.
Sources
Sudhanshu Dubey, Fake Software Update Abuses NetSupport Remote Access Tool, on fireeye.com, April 5 2018
Jérôme Segura, ‘FakeUpdates’ campaign leverages multiple website platforms, on malwarebytes.com, November 15 2018
Bryce Abdo et al, Head Fake: Tackling Disruptive Ransomware Attacks, on fireeye.com, October 1 2019

















