Blog
The New Economics of Ransomware
By BUFFERZONE Team, 8/08/2017
Ransomware is no longer just about the individual hacker. A new economic model, patterned after the marketing world, is fueling sophisticated ransomware campaigns. Ransomware-as-a-service is not only increasing the incidence of and variety of ransomware attacks but also making them harder to detect and defend from.
What is Ransomware-as-a-Service?
A ‘successful’ ransomware attack requires many components: beyond the software itself, which encrypts targets’ files and demands a ransom, a mechanism must be set up to receive payments, the ransomware needs to be packaged for delivery to target computers, and an exploit or social engineering campaign needs to be designed and implemented, often tailored with targets’ personal information for greater authenticity (spear phishing). Ransomware-as-a-service (RaaS) separates some of these components: a service provider provides the ransomware itself, with customization options, as a web service on the dark web. This enables individual attackers to create their own distribution and delivery campaigns for the provided software payload. Revenue – that is, the ransoms – is divided between the ransomware provider and the distributor.
The ransomware service is designed so that even attackers with just basic skills can start their own campaigns. An enterprising attacker creates an account in the provider’s website, sets the desired ransom and other parameters, and provides virtual wallet details. The web service provides a rich set of features, including various types of customization and a tracking portal for each attacker’s infections and payments. Here are a couple of examples of ransomware service sites, from the Satan and Karmen ransomware services, respectively
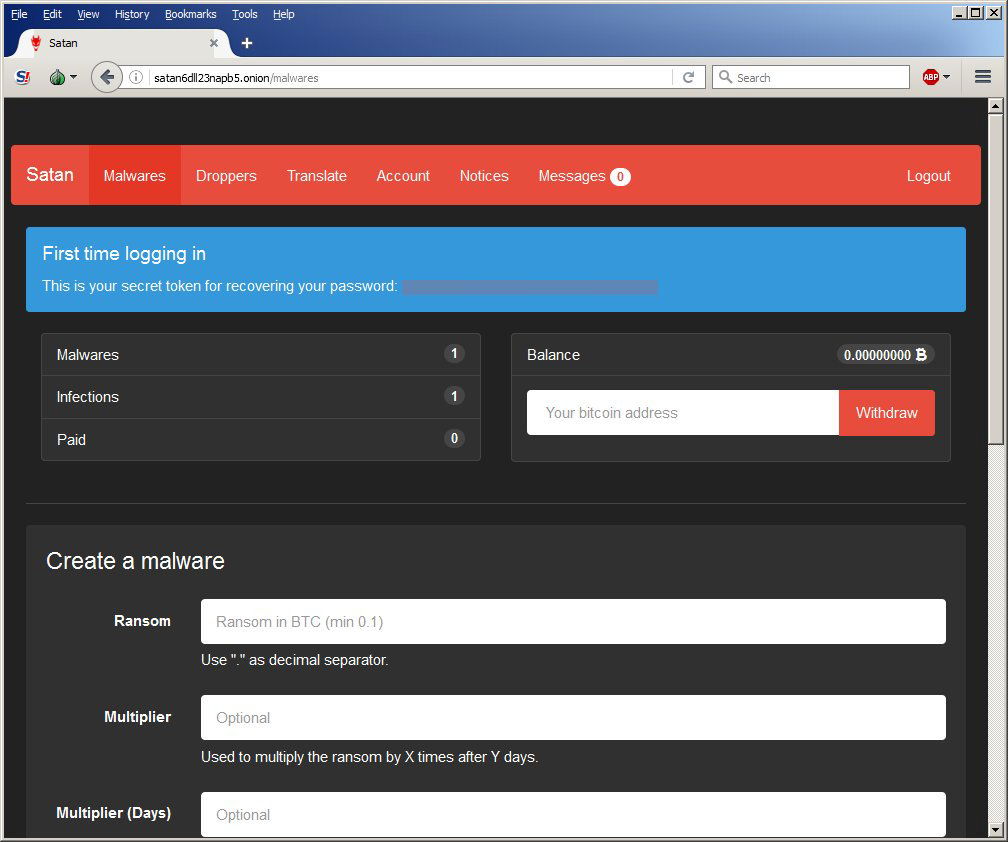
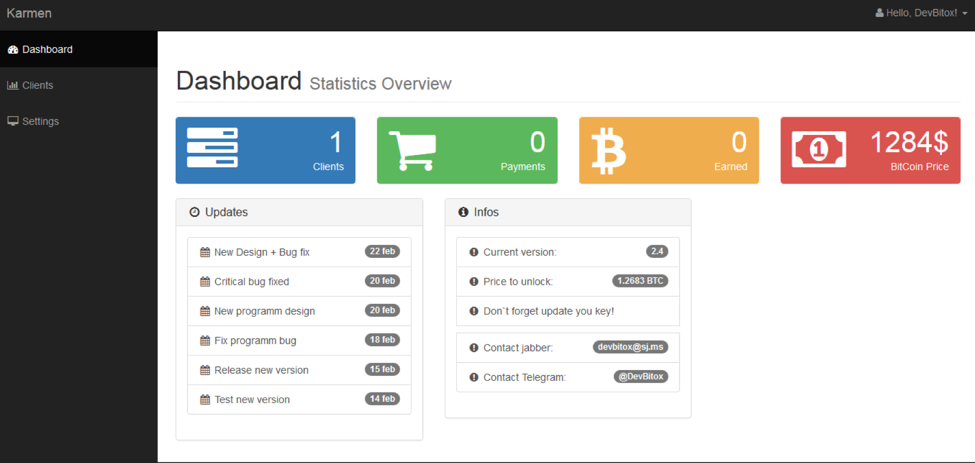
As you can see, these services are being managed like full commercial software services. These are just two of many known ransomware services, such as Cerber, Hostman, and Shark. It’s also likely that other ransomware packages that are appearing in different types of delivery mechanisms are the results of ransomware services that haven’t yet been publicly identified.
“Marketing” Advantages
Ransomware-as-a-service really took off beginning late 2016 and 2017. As an economic model, RaaS is patterned after affiliate marketing. Just as retailers share revenue (cost per sale) with affiliates who publicize and provide access to the merchants’ sites and products, the ransomware providers provide the core software and service to attackers who package and distribute the ransomware, and the providers take a percentage of the ransom.
For the cyber criminals, it’s a win-win situation: the ransomware creators get to leverage a wider set of distribution channels, and the individual attackers are relieved of the relatively more complex tasks of developing the software and managing the payments.
The Threat
So why should you care how exactly ransomware is provided and distributed? There are a couple of reasons. First, the RaaS model creates financial incentives for greater numbers of people to participate in attacks and to come up with new and creative ways of distributing the ransomware. Second, it means competition between ransomware providers, incentivizing them to continuously “improve” the ransomware itself to attract their customers (the attackers). The two factors combined mean increased versatility and adaptation of threats.
More and more people are becoming involved in the effort to circumvent security measures. Similar ransomware packages are appearing in customized flavors and varieties, and in completely different delivery mechanisms. So, even if your organization’s security products are handling current threats, it’s just a matter of time before a particular combination of attack vector, exploit kit and malware package gets around them.
So what can you do? Stop relying solely on gap-stopping, inspection-based security products that work by attempting to identify existing threats. Instead, use an isolation and containment product such as BUFFERZONE that isolates infectable areas from valuable resources.
BUFFERZONE creates a virtual container on organizational endpoints, and all processes that could access external, untrusted sources such as the internet are kept in the container, along with any data they download or save. At the same time, only uncontained processes can access trusted native endpoint and organizational files and other resources. The container is periodically wiped clean. So, even if ransomware does reach an endpoint, it can only encrypt recently downloaded files, for a short time, and is unable to do any real damage.
In fact, at one of the largest banks in Europe, security experts recently tested BUFFERZONE by intentionally infecting a computer with the WannaCry ransomware. Without performing any kind of inspection or signature identification, and withot depending on anything unique to WannaCry, BUFFERZONE successfully contained the attack and the ransomware was unable to encrypt and lock any files outside the container.
Sources
Xylitol, on twitter.com 1/18/17
Diana Granger, Karmen Ransomware Variant Introduced by Russian Hacker 4/18/17
Check Point Research Team, Anatomy of the Jaff Ransomware Campaign, on checkpoint.com 8/6/17
Bill Conner, Ransomware-As-A-Service: The Next Great Cyber Threat?, on forbes.com 3/17/17

















