Blog
New Phishing Campaign Uses Lure Image with External Links to Drop Malware
By BUFFERZONE Team, 10/10/2023
Target: IT Professionals
Tags: Anti-phishing, malware, isolation, Zero-trust
Research from Fortinet FortiGuard Labs [1] found a new variation of phishing/luring attacks that work by sending a Microsoft Office OOXML (Office Open XML) file. The file presents a deliberately blurred image and a counterfeit reCAPTCHA to lure the recipient into clicking on it. The Lure image [1,2] Clicking activates an embedded malicious link in the file “\word_rels\document.xml.rels,” as shown in Figure.1
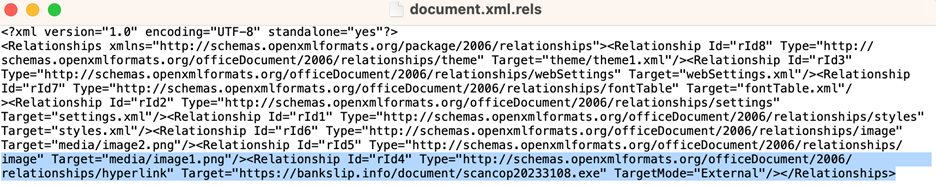
Figure 1. present the relations file named document.xml.rels. We can see that the TragetMode is External, and the target link contains a website with an executable as a resource.
As a result, the attack download, and executable initiate a chain of steps [1] in which three malware are downloaded. The problem starts with the low detection rate. After two days after the first submission, the detection rate was 15/62 engines. This is a significant red alert that although detection solutions are significant for endpoint protection, they are not enough. The solution is advanced prevention based on application isolation.
How to Prevent New Malware Attacks?
Attackers currently have the advantage of being able to test their modified attacks against a wide range of security solutions before launching them. This gives them a significant edge, making it clear that relying solely on detection is insufficient.
The answer is rooted not in detecting new attack variations but in its prevention. This is why we created BUFFERZONE® Safe Workspace™.
BUFFERZONE Safe Workspace™ is a comprehensive defense suite anchored in application isolation technology. This arsenal features the Safe Browser, SafeBridge® (boasting Content Disarm and Reconstruction functions), Safe Mail, and Safe Removable (geared towards thwarting USB-based attacks), all fortified with clipboard security. At its core, the Safe Workspace™ deploys a virtual container constructed by a kernel driver. This container bifurcates the operating system into dual logical realms:
Trusted Zone: A non-isolated region connected to the organization’s resources.
Untrusted Zone: Serving as a protective buffer, this zone enables various applications to run in isolation, cordoned off from the memory, files, registry, and processes of the trusted zone.
Safe Workspace™ is a reliable solution that allows users to access USB (Universal Serial Bus) files, email attachments, and downloaded content. It provides a protective virtual container that isolates potential threats from the broader environment, ensuring that malware cannot reach or compromise sensitive organizational data. The virtual container is periodically deleted and rebuilt; detection engines can scrutinize it for added security. By containing potential threats in isolation, BUFFERZONE prevents malicious entities from proliferating within an organization.
The answer is rooted not in detecting the zero-day attack but in its prevention. This is why we created BUFFERZONE® Safe Workspace™.
BUFFERZONE Safe Workspace™ is a comprehensive defense suite anchored in application isolation technology. This arsenal features the Safe Browser, SafeBridge® (boasting Content Disarm and Reconstruction functions), Safe Mail, and Safe Removable (geared towards thwarting USB-based attacks), all fortified with clipboard security. At its core, the Safe Workspace™ deploys a virtual container constructed by a kernel driver. This container bifurcates the operating system into dual logical realms:
Trusted Zone: A non-isolated region connected to the organization’s resources.
Untrusted Zone: Serving as a protective buffer, this zone enables various applications to operate in isolation, cordoned off from the memory, files, registry, and processes of the trusted zone.
Safe Workspace™ is a reliable solution that allows users to access USB files, email attachments, and downloaded content. It provides a protective virtual container that isolates potential threats from the broader environment, ensuring that malware cannot reach or compromise sensitive organizational data. The virtual container is periodically deleted and rebuilt; detection engines can scrutinize it for added security. By containing potential threats in isolation, BUFFERZONE prevents malicious entities from proliferating within an organization.
References
[1] Cara Lin, OriginBotnet Spreads via Malicious Word Document
, OriginBotnet Spreads via Malicious Word Document | FortiGuard Labs (fortinet.com)
[2] The Hacker News, Sophisticated Phishing Campaign Deploying Agent Tesla, OriginBotnet, and RedLine Clipper, https://thehackernews.com/2023/09/sophisticated-phishing-campaign.html

















