Blog
OneNote Malware Attack Prevention Using Content Disarm and Reconstruction
By BUFFERZONE Team, 5/06/2023
Target: Cybersecurity professionals
Tags: Microsoft Office, OneNote, Content Disarm & Reconstruction, Zero-Trust
Microsoft OneNote [1] is a versatile application included in the Microsoft Office suite, specifically designed for effortless information collection and seamless multi-user collaboration. It allows users to capture and organize their thoughts, ideas, and notes in a free-form manner. OneNote organizes information into pages, further structured into notebooks sections.
OneNote offers extensive functionality, enabling users to enhance their notes with multimedia recordings, file attachments, scripts, and hyperlinks. This versatility empowers users to create dynamic and interactive content within their notebooks.
However, it’s important to be cautious while using OneNote due to emerging security concerns. Recently, there has been an increase in the delivery of OneNote malware via email, as reported by Proofpoint [2]. Malware authors have exploited the file format associated with OneNote, which uses the extension “.one.” As a result, it is crucial to exercise caution when handling OneNote files received via email or other external sources to prevent potential security risks.
Figure. 1 illustrates the file format structure based on specification [1]:
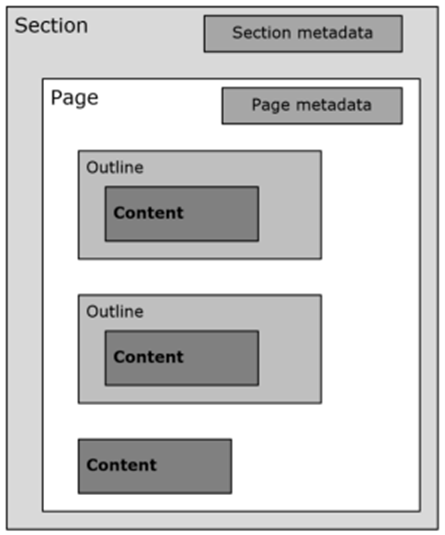
Figure 1. The figure is taken from [1].
The oneNote file structure is described in Figure 1; a “Section” is a container for specific sets of pages, metadata, and properties. The Metadata and properties are included in the section name. A “Page” is a container for user-defined content consisting of text, lists, tables, page titles, images, and note tags. An “Outline” is a container for most user-defined content such as text, lists, tables, etc. A “Property” set is a collection of properties representing some content. File Data Object is a binary data block containing pictures, embedded files, or audio/video content. “Notebook” is a collection of Section files stored in the same directory.
Recently Microsoft Researcher named Malwrologist released an open-source OneNote analyzer called pyOneNote [6]. The library makes it simple for researchers to research the file.
pyonenote –f 9c337d27dab65fc3f4b88666338e13416f218ab75c4b5e37cc396241c225efe8.one -o malonenote
It will open all embedded objects inside the malonenote folder, as shown in Figure 2.
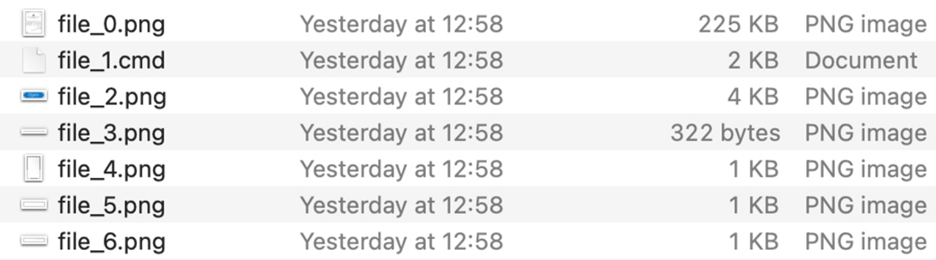
Figure 2. pyOneNote embedded files output.
We can observe that file_0.png and file_2.png are the lure images that try to convince the user to click and run the command line (file_1.cmd), as shown in Figure. 3.
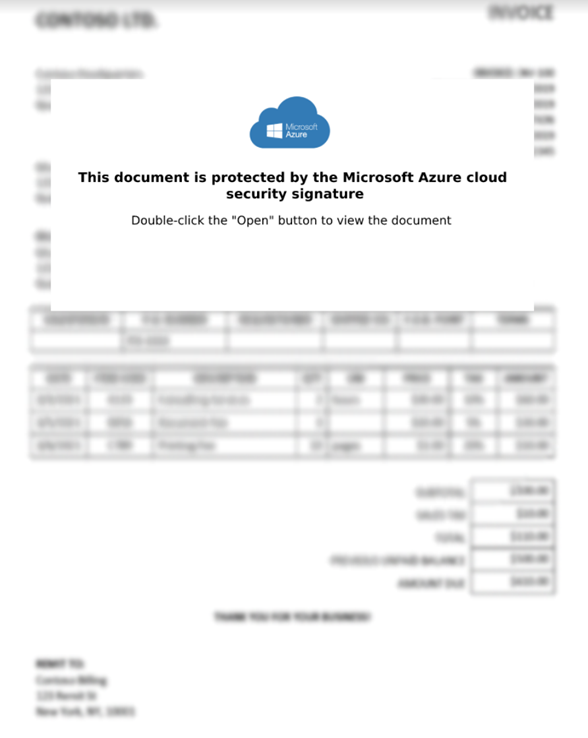
Figure 3. Main Lure image extracted from OneNote file.
Lure images are frequently employed in malware attacks to deceive users into clicking on malicious links, disabling security measures, and disregarding alerts. Despite the existence of notifications that aim to alert users upon clicking, research indicates that users often overlook them.
Malware can adopt various hiding techniques, such as concealing itself within file metadata [3], utilizing embedded images through steganography [4], residing within embedded files [2], or leveraging hyperlinks to redirect to remote sites [5]. Since detection methods are not 100% accurate, we at BUFFERZONE® advocate for a zero-trust approach to file security through Content Disarm and Reconstruction (CDR). CDR operates by comprehending the file format and all its potential attack vectors. Consequently, a CDR solution must sanitize different metadata sections of the file, disarm images, and recursively apply CDR to embedded objects like documents based on a predefined policy that disarms/sanitizes or removes suspicious content.
As depicted in Figure 4, the behavior exhibited after employing BUFFERZONE® CDR was successful in CDR the embedded images and removing the malicious script (CMD file).
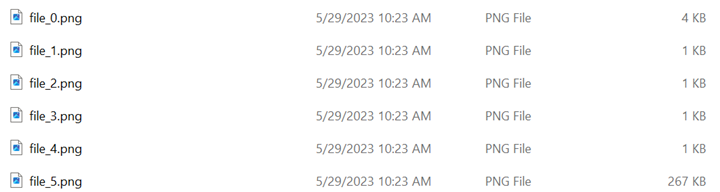
Figure 4. PyOneNote output after CDR
Figure 5 demonstrates the outcome of the file after undergoing Content Disarm and Reconstruction (CDR), revealing that the modified file retains its similarity to the original while ensuring enhanced security. This aspect holds significant importance as CDR is consistently applied to every file, regardless of detection outcomes, ensuring a proactive security approach.
With BUFFERZONE®, organizations can choose between automatic CDR for files or allowing users to work on files within the secure virtual isolation of the BUFFERZONE Safe Workspace™. Later, when a user wishes to transfer an untrusted file to the trusted zones within the organization, this can be effortlessly accomplished using BUFFERZONE SafeBridge® along with its CDR capabilities.
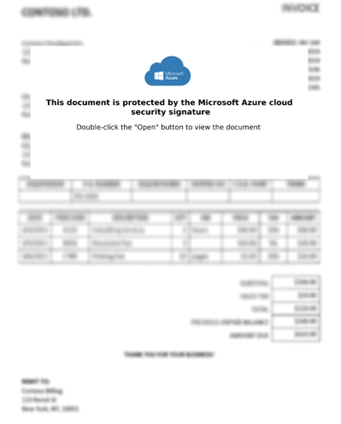
Figure 5. The resulting OneNote main lure image file After CDR is similar to the original lure image but is secured.
References:
[1] https://learn.microsoft.com/en-us/openspecs/office_file_formats/ms-one/73d22548-a613-4350-8c23-07d15576be50
[3] https://techunwrapped.com/how-cybercriminals-hide-malware-in-photo-metadata/
[6] https://github.com/DissectMalware/pyOneNote

















