Blog
Open Redirection: What is this phishing technique, and how do I defend against it?
By BUFFERZONE Team
Computer users are long accustomed to receiving emails notifying them of exciting business opportunities, great inheritances, lottery wins, packages that are waiting for them and many other
such messages that urge us to follow a link. But sometimes, the messages and the link targets can seem more trustworthy. When the target is a malicious site masquerading as a known, trusted site, that’s called phishing.
Phishing attacks are not limited to email and originate in many contexts, such as web pages, social media, and document files.
Attempts to get people to click on malicious links are an old practice of cybercriminals,
but in recent years they have turned it into a real art. By now, many users know to check link addresses (URLs), but these days even what seems to be a trustworthy address might lead to a false website.
The recently-published 2022 Verizon Data Breach Investigations Report indicates that phishing is one of the top five data breach vectors, accounting for almost 20% of breaches. And the Cloudian Ransomware Survey concluded that 65% of phishing victims had undergone anti-phishing training – which didn’t prevent them from being tricked into following a malicious link. Cyber criminals cleverly craft not only social-engineering messages, but even the link target URLs, so that even a security-aware user can be easily manipulated.
One of the ways URLs are made to seem legitimate is by taking advantage of Open Redirection.
What Is Open Redirect?
Open Redirect is a security flaw of web sites, where a site accepts a URL that includes a request for redirection to another site, and performs that redirection without verifying the target site’s legitimacy. The site might support redirection for legitimate purposes, but when the redirection is open to any destination address, attackers can use it to engineer malicious links that look legitimate.
Open Redirect is commonly used for legitimate purposes. For example, calendar links in Microsoft Teams may use redirections. An Open Redirect attack, on the other hand, allows an attacker to manipulate and deceive users by automatically redirecting them from a legitimate site to another, malicious site. Although Open Redirect is a well-known flaw, it is not considered a vulnerability. Open Redirect is legitimately used on the internet and is a common attack vector for phishing scams.
For example, it was recently reported that Google and Adobe open redirects are being used by phishing campaigns in order to add legitimacy to the URLs used in spam emails.
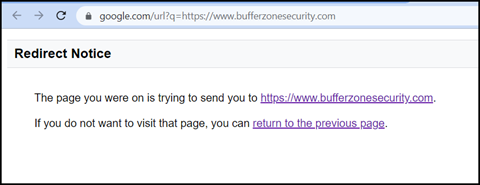
For example, imagine coming across the following URL:
https://www.google.com/url?q=https://www.bufferzonesecurity.com
By looking at the main, domain part of the URL, you can see that it is to google.com . However, in this case, clicking it will redirect you to BUFFERZONE’s site. In this case, that is of course a legitimate site, but another link might redirect to a malicious site.
To avoid phishing, trained users know to mouse over links to check URLs before clicking them. This action reveals the actual link target URL. However, in an Open Redirect attack this safety measure may fail, as the URL’s redirect action is not clearly apparent. In order to detect it, one needs to be aware of all the redirection tricks.
In order to try and mitigate such attacks, Google has added to the popular Chrome browser an indicator that a page is redirecting. The user is asked to confirm before moving to the new page:
However, since redirection is so common for legitimate purposes, users have become desensitized to such notifications and might routinely confirm the redirect without further examination. Leaving security up to user vigilance and detection is clearly not the solution. Instead, a new layer of browser protection is required to handle redirection threats and block phishing attacks.
Common Redirection Attacks
The key to identifying redirection attacks is understanding the various ways URLs define redirection. These include:
- RelayState: Depending on the architecture of the vulnerable site, redirection can occur following specific actions, such as logging in or page loading. For example:
example.com/login.html?RelayState=http://badsite[.]xyz
This link is to the login page of example.com, which is a legitimate, trusted site, in which the user has an account. Upon successful login, the user is immediately redirected to badsite[.]xyz . - Redirect URI: Researchers at Proofpoint recently discovered and reported on a set of previously unknown methods to launch URL redirection attacks against weak OAuth 2.0 implementations derived from a legitimate URL authentication. The report indicates that a malicious actor could register a sign-in OAuth application and set a redirect_uri parameter to a malicious URL. As a result, the victim would be redirected to the malicious site.
- Query redirection: A URL to a site that accepts redirection can include a redirection destination as a query defined by q= . For example:
example.com/view.php?q=https://badsite[.]xyz In this case, the application view.php is accepting the query string q=donotbrowse[.]xyz and redirecting to “donotbrowse[.]xyz”
Other parameters worth mentioning that can appear in URLs for redirections are: url, link, goto, gotoURL, outLink, and redirecturl .
- Redirection using @: A common redirection trick is to use @ after a legitimate domain. For example:
https://example.com@badsite[.]8xyz
How to avoid redirection attacks
Before clicking a link, mouse over it and check the structure of the URL. Ask yourself the following questions:
- Does the URL contain any of the redirection methods mentioned above?
- Does it contain multiple domains?
- Verify that the site is HTTPS secure
Once redirected, check:
- Does the URL in the address bar match the content of the page?
- Check the address domain in the whois If the domain created date is recent and the registry expiration is less than one year, this may be a temporary domain created by scammers.
In general, to defend against various attack types:
- Keep your browser up to date. Security patches are released for popular browsers all the time as a response to emerging attacks and vulnerabilities.
This kind of awareness and vigilance is important. However, human users are liable to miss things. BUFFERZONE is currently working to provide an automated, intelligent solution, by adding another layer to its SafeWorkspace™ solution. BUFFERZONE SafeWorkspace™ will combine antiphishing and antifraud protection with containment and content disarming. The BUFFERZONE Chrome and Edge browser extension will automate the threat research work and provide a smart layer of protection against redirection attacks and all types of phishing and brand exploitation.
Please follow us on Twitter and LinkedIn for the release date.
—
The writer is the Chief Technology Officer (CTO) of BUFFERZONE

















