Blog
Sophisticated Phishing Attacks Alert – How BUFFERZONE Can Stop It
By BUFFERZONE Team, 23/04/2023
Microsoft has issued a warning regarding a new phishing campaign aimed at accounting firms and tax preparers, which involves the use of remote access malware to gain unauthorized entry into corporate networks. As the United States is wrapping up its annual tax season, accountants are busy collecting clients’ tax documents to prepare and file their tax returns. This busy period presents an opportune time for threat actors to target tax preparers, hoping to trick them into opening malicious files that they may usually be more cautious with when they are not under time pressure.
Microsoft alerts against this new phishing attack targeting Tax firms against the phishing attack that install Remcos Remote Access Trojan (RAT) has they alert:
“With U.S. Tax Day approaching, Microsoft has observed phishing attacks targeting accounting and tax return preparation firms to deliver the Remcos remote access trojan (RAT) and compromise target networks beginning in February of this year”.
Microsoft summarize the new phishing campaign steps:
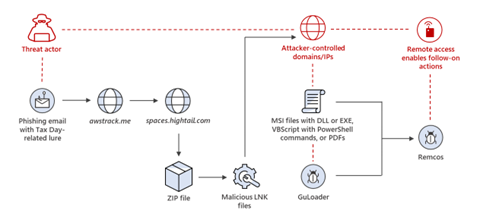
Image source: Microsoft
The phishing campaign deploys a strategy of using fraudulent tax documents sent by a “client” as bait, while the link contained in the email employs a reputable click-tracking service to avoid detection. Once the target clicks on the link, they are directed to a legitimate file hosting site, where the attacker has uploaded Windows shortcut files in the .LNK format. These LNK files generate web requests to actor-controlled domains and/or IP addresses to download malicious files. These malicious files then perform actions on the target device and download the Remcos payload, providing the actor potential access to the target device and network.
Cybercriminals frequently capitalize on current events and prominent news stories to orchestrate their attacks, utilizing social engineering tactics when people may be more susceptible to distraction or deception. So, this Tax phishing attack is only one out of many.
How BUFFERZONE ® Safe Workspace® Protects You
The BUFFERZONE security solution offers a two-layered approach to safeguarding your organization against malicious phishing attacks. The first layer comprises the BUFFERZONE anti-phishing browser extension, which utilizes advanced Artificial Intelligence algorithms to detect and identify phishing attempts. When a suspicious or harmful phishing page is detected, we immediately alert the user and prevent the phishing page from loading.
The second layer is BUFFERZONE virtual isolation. BUFFERZONE® creates trusted and untrusted zones:
- Untrusted Zone: Virtual secured environment that isolates removable media (USB), browsers, email links, and attachments. BUFFERZONE® enables the user to securely open and work on documents without the risk of ransomware.
- Trusted Zone: Your real environment connected to all your organization’s resources. This zone is separated from the Untrusted Zone, and data cannot be copied to the Untrusted zone.
The browser is isolated in the untrusted zone meaning the malware cannot lateral movement inside the computer and it is locked inside BUFFERZONE’s virtual container and cannot run remote code execution in the operating system.
When the user would like to save its work, he can securely use BUFFERZONE SafeBridge.
BUFFERZONE SafeBridge® is a content disarm and reconstruction engine that recursively removes malicious attack vectors from files, images, and videos. There is no need for internet connectivity; all files are disarmed in the virtual container and safely moved, if needed, to the Trusted Zone. In this example the downloaded file will be contained inside the untrusted zone, the infection steps will fail, and the attack cannot install the Remcos RAT. BUFFERZONE solution is isolating the malware activity in the untrusted zone, enabling security detection solution to scan the content of the container.

















