Blog
What Is Content Disarm and Reconstruction?
By BUFFERZONE Team, 4/05/2023
Tags: Malware Analysis, CDR, Zero-Trust, Detection
Audience Tag: Feature Spotlight
Over 92% of cyber-attacks start with seemingly harmless emails or links? According to a report [1], the number of malicious new files per day has increased by 5.7%, reaching a staggering 380,000 malicious new files per day. With detection methods not being 100% foolproof, a new file security solution is urgently needed.
The ever-increasing volume of malicious files being circulated poses a significant threat to organizations. Cybercriminals are constantly finding new ways to disguise malware and evade detection, making it crucial for organizations to adopt advanced security measures. Relying solely on traditional antivirus software and other conventional security measures may not provide adequate protection against these rapidly evolving threats.
To effectively combat this growing menace, organizations need innovative solutions to reduce the attack surface and Content Disarm and Reconstruction (CDR) is a powerful solution. CDR takes a proactive approach by dissecting files and documents, analyzing their components, and reconstructing them to remove potentially harmful elements. By neutralizing potential threats in files, CDR helps prevent malware from infiltrating systems through evasive lure emails, links, or file attachments.
In the following Figure we can observe a typical file that contains different attack vectors.
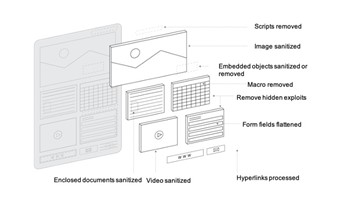
Fig. 1 Typical document illustration that contains attack vectors [2].
The attack vectors may be hyperlinks, macros, known exploits, images and other media components.
While Content Disarm and Reconstruction (CDR) is an effective cybersecurity technique, it does have some limitations. During the disarm process, certain file objects may be removed, and active components may be disabled, which can impact the functionality of the resulting file. However, recent academic research [2] has shown that CDR is highly effective in terms of malware disarm rate and is able to remove threats based on detailed validation against multiple antivirus engines, such as VirusTotal.
One concern with CDR technology is the similarity between the original file and the CDR-reconstructed file. Some studies have shown that the resulting files after CDR may be highly similar, which could raise concerns about potential residual threats. However, it is important to note that CDR solutions are continuously evolving, and newer techniques are being developed to mitigate this concern and improve the similarity between the original and reconstructed files.
Another limitation of CDR is that some solutions may require internet access (Software-as-a-Service or SaaS), which could raise concerns about privacy and data security. In certain scenarios, private files may be shared with third parties during the CDR process, which may not be desirable for organizations that prioritize data privacy and confidentiality.
It is important for organizations to carefully evaluate and choose CDR solutions that align with their specific security requirements and risk tolerance. While CDR can be a valuable addition to a comprehensive cybersecurity strategy, it is essential to be aware of its limitations and choose solutions that offer the right balance between security and functionality and comply with privacy and data protection requirements.
BUFFERZONE SafeBridge™ CDR
Currently, Content Disarm and Reconstruction (CDR) solutions are typically deployed in either public cloud or private cloud environments. However, BUFFERZONE CDR stands out as the only vendor that runs CDR within a secure isolated container. This approach reduces latency, eliminates the need for special connectivity, and is cost-effective.
With BUFFERZONE CDR, downloaded files can be automatically subjected to CDR automatically or based on user desire since user may want to work inside the BUFEERZONE® secure container. Furthermore, BUFFERZONE offers Microsoft Outlook email plugin that CDR all incoming and outgoing emails based on organization configuration. This ensures that every email and downloaded file goes through CDR to remove potential threats and enhance security, without the need for any additional configuration. BUFFERZONE CDR works seamlessly with every downloaded file.
One of the key advantages of BUFFERZONE CDR is its integration with BUFFERZONE Safe Workspace®, without incurring any additional costs. This means that organizations can benefit from a comprehensive security solution that combines CDR with isolated workspace protection, providing a robust defense against cyber threats.
In conclusion, BUFFERZONE SafeBridge™ CDR offers a unique approach to content disarm and reconstruction. Running within a secure isolated container, on the host, and as an integral part of BUFFERZONE Safe Workspace™. This provides organizations with a highly effective and efficient solution for securing downloaded files and emails, without the need for special connectivity or additional configuration. Although detection solution exists, they are not 100%, as a result organization must reduce their attack surface based on smart endpoint isolation and CDR. It is proven that CDR can provide an additional layer of defense and significantly improve the organization defense methodology.
BUFFERZONE Safe Workspace® offers a novel and robust approach to content disarm and reconstruction, operating within a secure isolated container on the host. This innovative solution provides organizations with a highly effective and efficient means of securing downloaded files and emails, without the need for complex connectivity or additional configuration. While detection solutions may have limitations, organizations can augment their defense strategy by leveraging smart endpoint isolation and CDR, which has been proven to enhance overall security and significantly reduce the attack surface.
[1] Kaspersky, “New malicious files discovered daily grow by 5.7% to 380000 in 2021”, 2021. https://www.kaspersky.com/about/press-releases/2021_new-malicious-files-discovered-daily-grow-by-57-to-380000-in-2021
[2] R. Dubin, “Content Disarm and Reconstruction of RTF Files A Zero File Trust Methodology,” in IEEE Transactions on Information Forensics and Security, doi: 10.1109/TIFS.2023.3241480.

















