Blog
The Beginners Guide to Chrome Extension Research
By BUFFERZONE Team, 2/07/2023
Target: Cybersecurity specialist
Tags: CRX, Chrome Extension, Malware, Reverse Engineering.
A Chrome extension is a small software program that enhances the functionality of the Google Chrome browser. Extensions are made using web technologies such as HTML, JavaScript, and CSS and are designed to make the browsing experience more efficient and enjoyable.
Some extensions provide utility features like ad-blocking, language translation, password management, or note taking. Others can change the appearance of your browser, provide quick access to certain websites, or enable more advanced features like developer tools
While Chrome extensions can provide a lot of utility and enhance your browsing experience, they can also pose certain security risks if not used carefully:
- Malicious Extensions: Some extensions can be malicious, either because they were designed that way, or because they were once benign but were later bought and modified by malicious parties. These extensions can steal your personal data, inject ads into websites you visit, or even install malware on your device.
- Overly Broad Permissions: Chrome extensions need certain permissions to function, but some might ask for more permissions than they need. Granting these permissions can give the extensions access to your browsing data, personal information, or even control over all the pages you visit.
- Data Breaches: Even if an extension is not deliberately malicious, it might still be a security risk if its developers do not follow best practices for data security. If the extension collects or transmits sensitive information and it does not do so securely, that information could be at risk.
- Lack of Updates: If extensions are not regularly updated, they may become susceptible to known security vulnerabilities over time.
Several high-profile attacks were generated throw Chrome extensions recently:
- Wide-scale theft and redirection attack: More than two dozen browser extensions, primarily designed as video downloaders, were found to steal personal information, redirect users to ads or phishing websites, and even install malware. This large-scale attack impacted about 3 million users. The extensions exhibited malicious behavior days after installation, making it difficult for security software to discover. They also logged every link a user clicked, sent that information to remote servers, and collected personal data. In some cases, these extensions could download further malware onto a user’s PC [1].
- Malicious extension installation via compromised systems: In some cases, malicious extensions were installed by adversaries who had already compromised a system. Once installed, these extensions could browse websites in the background, steal all the information a user entered into a browser, and be used as an installer for a RAT (Remote Access Trojan) for persistence. There have also been instances of botnets using a persistent backdoor through malicious Chrome extensions [2].
- ChromeLoader/Shampoo attack: The ChromeLoader campaign used a malicious extension called “Shampoo,” which tricked victims (primarily users of movie and video game pirating websites) into installing it. This extension redirected users’ search queries to malicious websites. The malware was designed to relaunch itself via the Task Scheduler on victims’ machines every 50 minutes, making it challenging to get rid of due to multiple persistence mechanisms. The extension was heavily obfuscated and contained many anti-debugging and anti-analysis traps [3].
How to mitigate the risk?
It is recommended to only install extensions from trusted sources (preferably the Chrome Web Store), to carefully review the permissions that an extension asks for, and to keep extensions updated. Also, regularly review and remove any extensions that you no longer use. Using security software that includes an internet security component can also help to alert you to potential threats.
Chrome extension research
In this blog we will use ExtAnalysis [4] is a Chrome extension analysis framework that can perform the following actions:
- Download & analyze extensions: This includes extensions from the Chrome Web Store, Firefox Addons, and installed extensions of Google Chrome, Mozilla Firefox, and (in the future) the Opera Browser. Extensions in the formats of .crx, .xpi, and .zip can be uploaded and scanned.
- View basic information: Such as Name, Author, Description, and Version of the extension. It also allows you to view the manifest and detailed permission information.
- Extract threat intelligence from files: This includes URLs, domains, IPv6 and IPv4 addresses, Bitcoin addresses, Email addresses, file comments, and Base64 encoded strings.
- View and edit files: You can view and edit HTML, JSON, JavaScript, and CSS files.
- VirusTotal scans: This tool can perform VirusTotal Scans for URLs, Domains, and Files, and it can also conduct a RetireJS Vulnerability scan for JavaScript files.
- Reconnaissance tools: It provides tools for Whois Scan, HTTP headers viewer, URL Source viewer, and GEO-IP location for extracted URLs.
- Graph insights: View the entire extension files and URL relationships.
In this article, we delve into an investigation of DealPly adware with the MD5 hash value: 38a7b26c02de9b35561806ee57d61438. Typically, users install Chrome extensions inadvertently while downloading pirated content from disreputable websites [5]. Upon installation, this extension modifies the browser’s homepage, supplants the default search engine, and analyses user search queries to produce more customized ads. When we decompress the Chrome extension, the file “AmpSearchServiceLocalList.json” reveals the primary keyword logic. Employing the ExtAnalysis platform’s graph feature, we can visually represent the full connection layout:
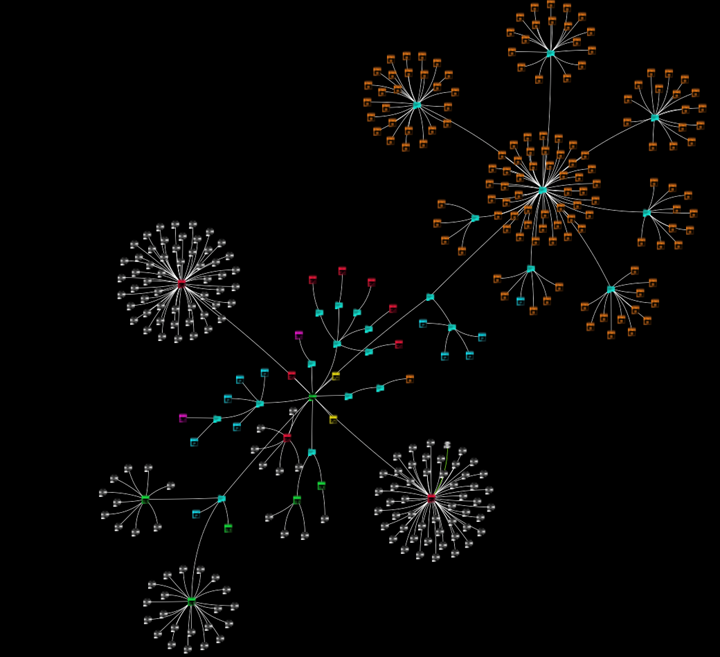
And the Json and the webpages related to him:

The red square is the JSON file with multiple related website links that the “new” search engine refers to.
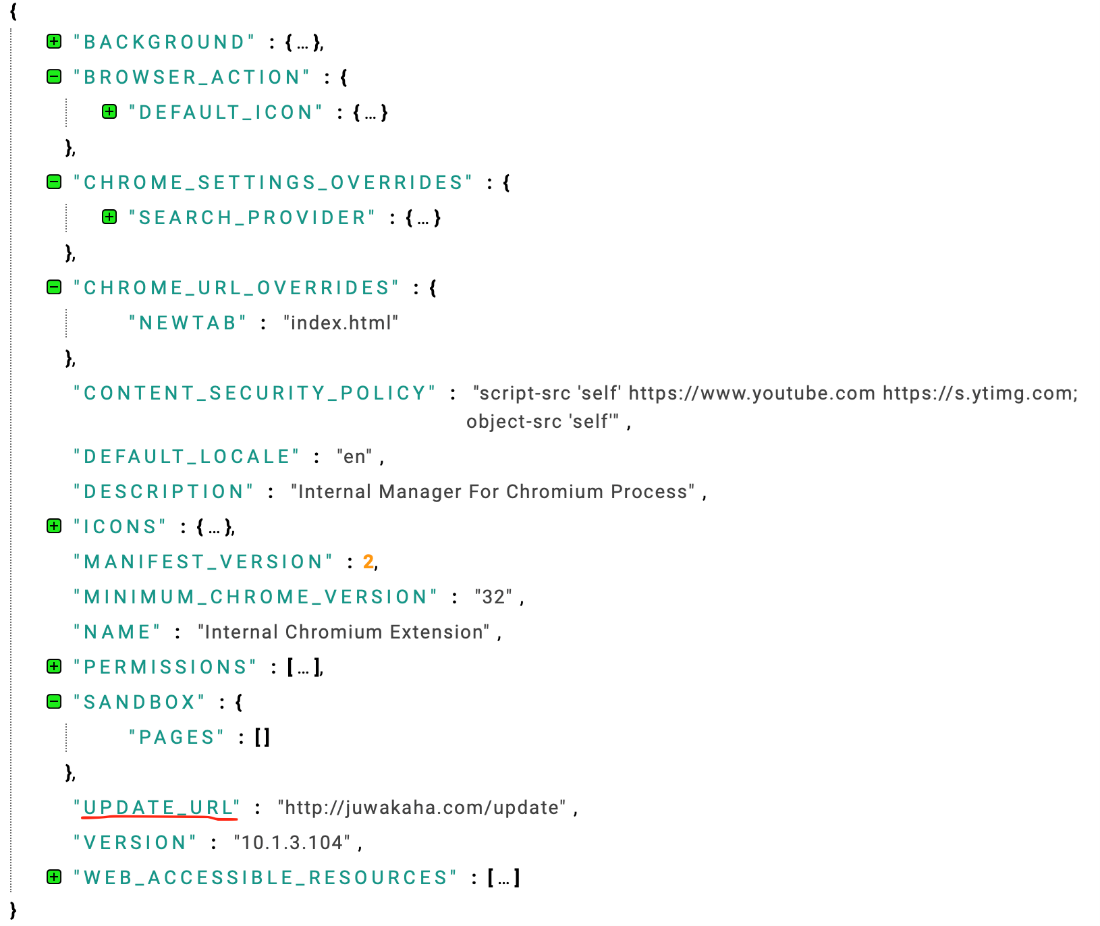
Upon examining the manifest.json of the Chrome extension, we noticed an aberration: the “UPDATE_URL” path indicates that the extension does not follow Google Chrome webstore’s standard update mechanism. Instead, it uses an update link from a suspicious website, “juwakaha.com”. This deviates from the usual path, which is typically “https://clients2.google.com/service/update2/crx”. This discrepancy serves as a red flag, suggesting that the latest updates are not undergoing Google’s validation process, but are being updated by the questionable website. This circumstance aligns with the fact that the extension is being updated externally, beyond the purview of the official marketplace.
When we turn to validate the Chrome extension permission, we can see that:
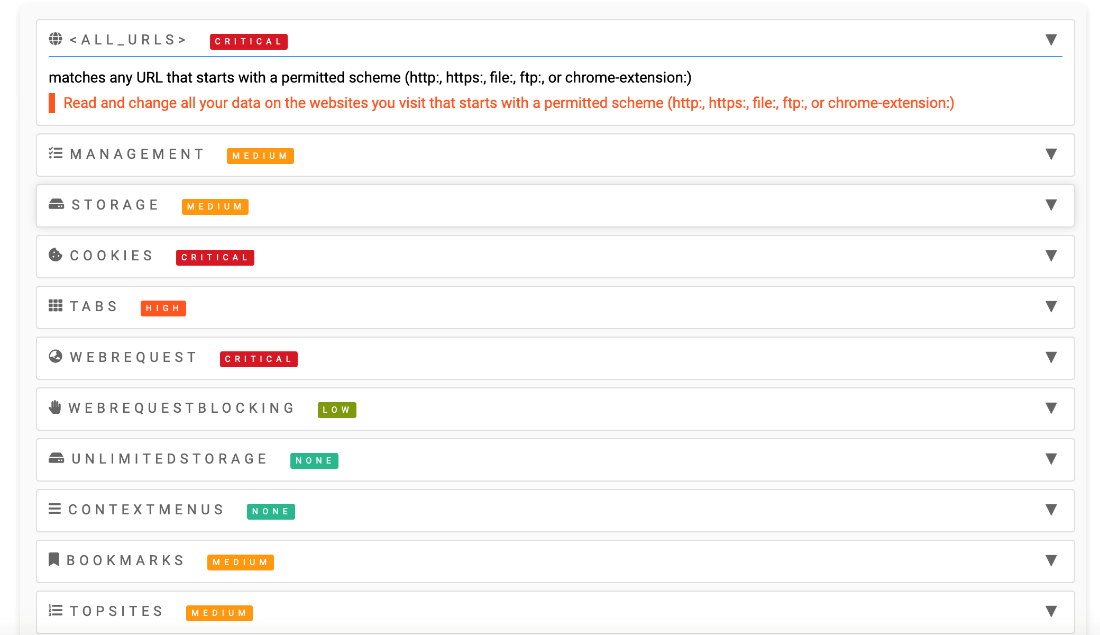

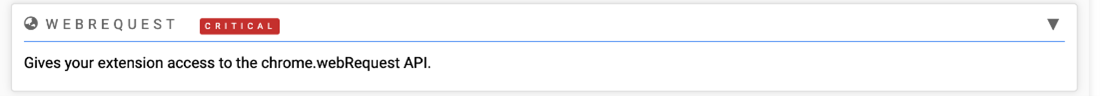
Upon analysis, it becomes apparent that the extension possesses the capability to modify all data on websites during any browsing session, gain access to cookies, and utilize the Chrome.WebRequest API. While not every application exhibiting such permissions is necessarily malicious, their presence is cause for concern and warrants further scrutiny.
Summary
In this article, we apply static analysis to a Chrome extension using the ExtAnalysis platform. We illustrate how inspecting the extension’s manifest, assessing its permissions, and understanding its network graph can streamline our investigation and provide crucial insights. These initial procedures serve as an excellent foundation before we delve into the more intricate task of analyzing the JavaScript code.
We hope you enjoyed this blog.
Try us now!
References:
[1] Paul Wagenseil, Malicious Chrome and Edge extensions infect at least 3 million people — what to do, https://www.tomsguide.com/news/28-bad-browser-extensions.
[2] MITRE, Browser Extension, https://attack.mitre.org/techniques/T1176/
[3] Craig Hale ,This malicious Google Chrome extension could hijack your devices if you try and download pirate movies, https://www.techradar.com/news/this-malicious-google-chrome-extension-could-hijack-your-devices-if-you-try-and-download-pirate-movies
[4] Tuhinshubhra , Chrome Extension analysis framework, https://github.com/Tuhinshubhra/ExtAnalysis
[5] KASPERSKY , Threat in your browser: what dangers innocent-looking extensions hold for users, https://securelist.com/threat-in-your-browser-extensions/107181/



















